SIEM knowledge base
Security information and event management (SIEM) defined
A SIEM solution is an enterprise-level application that centralizes and automates cybersecurity-related operations. The tool helps combat cyberattacks by collecting, analyzing, and correlating network events aggregated from various entities in an organization's IT infrastructure.
SIEM solutions emerged in the early 2000s to address the need for centralized security monitoring. By 2029, the SIEM market size is projected to reach $17.07 billion, with industries like finance, healthcare, IT, and the public sector leading SIEM adoption.
- Gartner introduced the acronym SIEM in 2005, consolidating the capabilities of security information management (SIM) and security event management (SEM).
- SIEM solutions can process massive amounts of data in real time, exceeding even several thousands of events per second (EPS).
- In addition to security operations, compliance with regulations represents a significant use case for a SIEM solution. The tool facilitates log retention and automates audit report generation, aiding organizations in meeting mandates effectively.
Understanding SIEM
Comparable to a surveillance console that helps you monitor and assess dangers in the physical space of your organization, a SIEM solution is like a virtual security command center that provides complete, real-time visibility into your enterprise networks.
Building upon this visibility, a SIEM solution offers threat detection, investigation, and response (TDIR) capabilities through security analytics, event correlation, ML- and AI-based anomaly detection, and incident response workflows.
Why is SIEM necessary for network security when there are defense measures such as firewalls, IDSs, IPSs, and antivirus solutions?
A network can have the most advanced perimeter defenses, but all it takes is a single misconfigured rule to open the network up to attacks. This is where continuous, real-time monitoring and correlation of security events through a tool like a SIEM solution saves organizations from million-dollar breaches and ransomware attacks that seem to come out of nowhere.
Learn moreWho uses SIEM solutions?
Cybersecurity professionals use SIEM solutions to secure enterprise networks of varying sizes across industries. These professionals primarily include security operations center (SOC) teams comprised of analysts responsible for identifying and responding to security incidents.
SOC analysts investigate alerts generated by a SIEM solution, prioritize them based on severity, conduct forensic analysis, and mitigate threats swiftly. Modern SIEM tools play a major role in advanced persistent threat (APT) detection, catering to various use cases of SOCs.
Learn moreSIEM in cybersecurity: Where does a SIEM solution fit in the world of cybersecurity tools?
SIEM vs. EDR vs. XDR vs. SOAR
While SIEM solutions were the first to emerge, endpoint detection and response (EDR) solutions emerged in the mid-2010s in response to the increasing sophistication of endpoint threats, aiming to provide real-time detection at the endpoint level.
Extended detection and response (XDR) solutions evolved in the late 2010s to address the need for broader threat visibility and correlation across multiple platforms. Around the same period, security orchestration, automation, and response (SOAR) emerged as a notable solution, simplifying incident response procedures through automating and orchestrating security operations.
Though each of these solutions caters to specific use cases, a SIEM solution acts as the hub, aggregating outputs from these tools and facilitating centralized monitoring.
Learn moreThe feature suite overview of SIEM
Log management
- Automated log collection
- Log parsing and normalization
- Log archival
- Log forensics offered through log search
Threat detection
- Correlation rules
- Alert criteria and profiles
- UEBA
- Threat feed integration for IOCs
Threat remediation
- Incident management console
- Automated response workflows
Security analytics
- Predefined repositiory of reports for devices and applications
- Active directory reports
- UEBA reports
- Trend reports
- Compliance specific reports
- Dashboards
- Advanced investigation console
Threat hunting
- Process hunting trees
- Mitre ATT&CK framework integration
- Advanced threat analytics
How does a SIEM solution work?
The architecture of a SIEM solution, the capabilities involved, and the associated features: An overview
1. Network data aggregation
A SIEM solution collects logs through agent-based methods (where agents are deployed on network devices, servers, and endpoints), syslog (which forwards logs to a central server), and APIs (which enable direct integrations with supported systems).
Legacy SIEM solutions primarily relied on log-based data collection from limited sources. Modern SIEM solutions incorporate diverse data sources, such as logs, packets, traffic flows, cloud services, and APIs, for comprehensive threat visibility and detection accuracy.
SIEM logging and data aggregation: What are the types of data collected from different network entities, and what insights can be gained from them?
| Network entities | Types of logs collected | Insights |
|---|---|---|
| Routers | Configuration change logs, interface status logs, and flow logs | Network traffic patterns, routing changes, and potential DDoS attacks |
| Firewalls | Configuration logs, connection logs, VPN logs, and proxy server logs | Unauthorized access attempts, configuration changes, blocked connections, and policy violations |
| Web servers | Application logs and access logs | HTTP requests, web application attacks like cross-site scripting, and access to sensitive pages |
| Endpoints | System logs, security logs, application logs, and network logs | Malware infections, software installations, and user activity |
| File servers | User access logs, system event logs, file modification logs, and authentication logs | Suspicious user access, configuration and permission change anomalies, unauthorized file changes, and excessive modifications |
| Cloud platforms | API access logs, audit logs, resource usage tracking logs, instance provisioning logs, and application usage logs | Unauthorized data sharing and API calls, spikes in resource consumption, intrusions, infrastructure changes, and application performance |
2. Data processing
Once collected, the raw data undergoes processing, which includes indexing, parsing, and normalization. Logs are indexed for fast retrieval, parsed to extract relevant information, and normalized to ensure consistency across different formats.
Legacy SIEM systems employed rule-based parsing and indexing, leading to rigid structures. Modern SIEM systems leverage ML algorithms, like supervised learning, unsupervised learning, and natural language processing, for dynamic parsing. Top-tier SIEM solutions are capable of processing over 500,000 EPS in optimal conditions.
3. Storage and retention
Processed data is stored in a centralized repository, which could be a dedicated database, data lake, or cloud storage solution. This repository must support scalability and high availability to accommodate large volumes of data and ensure data integrity. SIEM solutions also help you retain the necessary logs for forensic analysis and audit purposes.
Legacy SIEM systems used relational databases for storage. Modern SIEM systems employ distributed storage solutions like Hadoop or Elasticsearch for scalability and real-time data access and retrieval.
4. Data visualization and reports
One of the primary use cases of a SIEM solution is data visualization, which presents network and security insights through graphical reports and dashboards. This aids analysts in understanding network events, observing malicious activity trends, and ascertaining the organization's compliance status.
Modern SIEM solutions offer interactive, customizable dashboards for intuitive data visualization. They automate compliance reporting and provide detailed insights and real-time monitoring, facilitating alignment with evolving and newly launched regulations and standards. This is a significant advancement from legacy solutions' static reports.
Compliance auditing in SIEM
Businesses are required to comply with IT regulations. A SIEM tool simplifies the entire audit process, minimizing security risks and easing compliance demonstration for enterprises by providing out-of-the-box, audit-ready reports for various compliance standards: the PCI DSS, the GDPR, HIPAA, FISMA, SOX, FERPA, NERC CIP, the PDPA, and more. Some SIEM solutions also enable users to customize or create new compliance reports based on their auditing requirements.
Learn more5. TDIR
Threat detection
A SIEM solution's core function is to correlate parsed data and find threat patterns, and this is offered through predefined correlation rules for common threats, ransomware attacks, suspicious process spawning, the use of attacker tools, and more.
Modern SIEM solutions also use ML-based behavioral and statistical analysis to establish baselines for users and entities in order to find true anomalies diverging from the observed patterns. Once such anomalies are detected, a SIEM solution sends alerts through email and SMS. A dedicated alert dashboard is available for you to configure, manage, assign, and resolve alerts.
Event correlation in SIEM
Correlation engines employ rules, which are sequences of events that could indicate security threats. A modern-day SIEM solution uses non-event data and threat feeds to enrich its correlation engine's efficiency. As customizable platforms, SIEM solutions offer users the ability to fine-tune correlation rules to capture threats that are specific to an enterprise.
Learn moreUEBA in SIEM
A SIEM tool's UEBA feature detects abnormal behavior in an organization's network using ML and deep learning algorithms. By collecting data related to user and entity activities in the network, the tool creates baselines. When it detects any deviation in a user or entity's behavior in comparison with the baseline behavior, it assigns a risk score based on the severity. Deviations can include logins at unusual hours, excessive login failures within a short time frame, and privilege escalation.
Security administrators get notified in real time if a risk score crosses a certain threshold. The ML-driven UEBA component of a SIEM solution captures APTs, which often go undetected when only a rule-based detection mechanism is employed. UEBA also plays a major role in detecting insider threats, account compromise, and data exfiltration.
Learn moreThreat investigation
A SIEM solution's alert dashboard accumulates all the suspicious events that need to be investigated. You can obtain the basic event details of who, what, when, and where from the alert dashboard itself. To investigate further, analysts use the log search capability to construct search queries and dig deep. Modern SIEM solutions have a dedicated console that assists with guided investigation; they also provide useful integrations, like with the MITRE ATT&CK® framework to help you conduct proactive threat hunting activities.
Learn moreIncident management and response
A SIEM solution gathers all the detected incidents and presents the timeline and critical data points on a dashboard so you can monitor, build evidence about, triage, and resolve incidents from a single console. You can associate predefined workflows with alerts to automate incident response. The workflows include actions like shutting down systems, killing a process, and disabling a user. These can be constructed in a sequence for immediately responding to an attack and reducing its impact.
Learn more6. Advanced integrations
The way ahead for SIEM solutions entails integrating with various IT and security tools to enhance operational efficiency and achieve centralized security management in order to improve organizations' overall cybersecurity postures.
Here are some examples:
| Purpose | Integrations |
|---|---|
| IT infrastructure management | ITOM and IAM tools |
| Cloud security | Cloud access security brokers (CASBs) and cloud data loss prevention (DLP) tools |
| IT security monitoring and automation | XDR, EDR, SOAR, and UEBA tools |
| Threat intelligence | Global threat feeds like LevelBlue Labs Open Threat Exchange, VirusTotal, and Constella |
| Threat hunting frameworks | MITRE ATT&CK and YARA (the insights from the frameworks can be integrated into a SIEM solution's reports, alert logic, and response workflows) |
| SOC operations | Ticketing tools like Jira Service Desk, Zendesk, Freshservice, and ManageEngine ServiceDesk Plus to assign incidents to analysts |
CASBs in SIEM
CASBs use an organization's security policies to inspect the data transmitted between a cloud service provider and the organization. For instance, if employees store sensitive corporate data in unsanctioned cloud applications, CASBs assist IT teams in identifying all the unmanaged applications accessed by users and in implementing remedial measures. Integrating a SIEM solution with a CASB offers IT admins a holistic view of cloud security, enhancing threat detection and establishing coordinated incident response.
Learn moreMITRE ATT&CK in SIEM
MITRE ATT&CK is an open-source framework that categorizes and describes adversary tactics, techniques, and procedures. There are 14 tactics, with multiple techniques under each. They describe how an attacker gains initial access to a network, moves laterally, and escalates their privileges to exfiltrate data and install backdoors. The insights from this framework are integrated into a SIEM solution's reports, alerts, and response workflows.
Learn moreLooking for a personalized demo of a SIEM solution ?
Ask, learn and understand how a SIEM can help your business
Connect with our expertsTake a peek at how SIEM is used to identify and respond to malicious activities with an actionable threat detection and remediation workflow
Scenario
Consider the case of an investment firm encountering compliance penalties as a result of a track record of file integrity breaches originating from either insiders or external actors.
Action plan
The firm has to strictly monitor access to its sensitive files and find user accounts exhibiting suspicious behaviors, such as excessive file permission changes and file deletions.
Here's a sample workflow the firm can implement by deploying a SIEM solution in its environment:
- Configuring a correlation rule for file access failures
- Getting notified via email
- Using the alert dashboard to assign tickets to analysts
- Verifying alert details and investigating
- Immediately performing remedial actions
- Investigating further
Configuring a correlation rule for file access failures
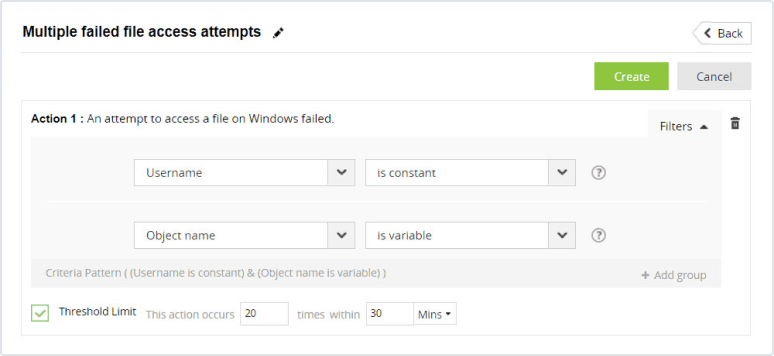
SIEM solutions have correlation rule packages that SOC analysts can simply enable or customize. In this scenario, let's assume that a rule has been enabled to detect multiple failed file access attempts from a single user. The SOC analyst can customize this rule by adding a threshold for the number of observed events within a short span of time to reduce false positives.
Getting notified via email
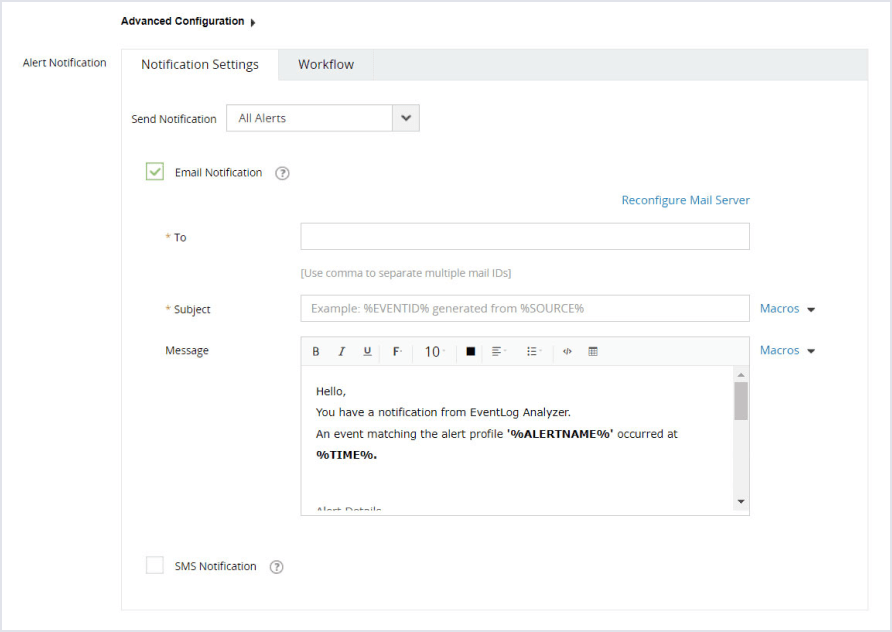
Since this is a critical alert for the investment firm, the SOC analyst can configure an email or SMS notification for it.
Using the alert dashboard to assign tickets to analysts
The analyst is now notified when a user fails to access multiple files. Using the alert dashboard, the analyst can assign people to handle different incidents. SIEM solutions integrate with ticketing tools like ServiceNow, ServiceDesk Plus, and Jira Service Desk for collaborative work.
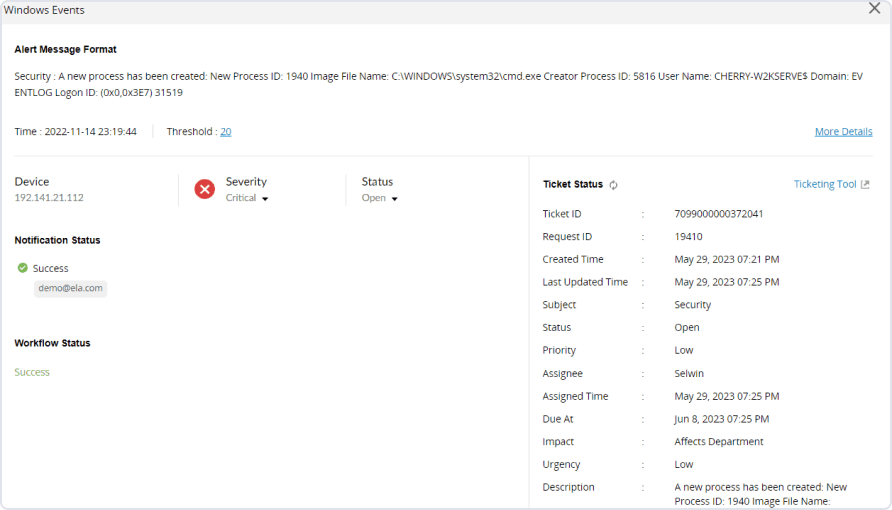
Verifying alert details and investigating
The alert dashboard can be utilized to dig deeper into the who, what, when, and where of the events.
An event can be further investigated through insights from a contextual analysis console to ascertain if it's a truly malicious event. UEBA can be used to check the risk score of the user involved.
Immediately performing remedial actions
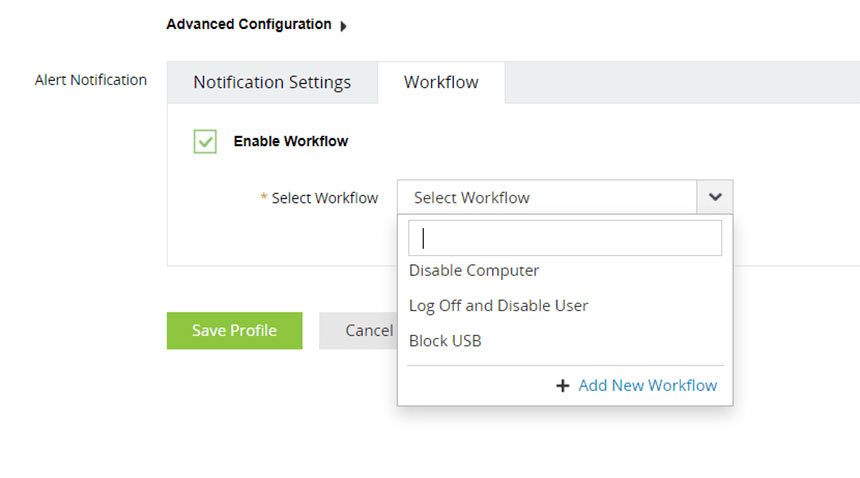
Analysts can associate a response workflow with alerts about what are certain to be threats. In this example, logging out and disabling the user are appropriate responses. SIEM solutions provide analysts with workflow actions, such as killing a process, shutting down systems, modifying firewall rules, and blocking USBs. These actions can be used to create a custom workflow and associate it with alerts.
Investigating further
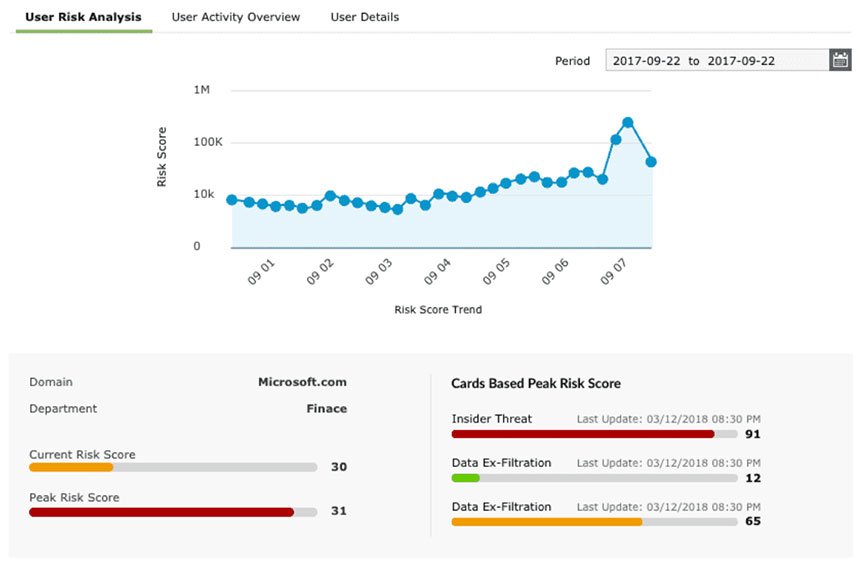
Once remedial actions are taken, the analyst can dig deeper and investigate through predefined reports, log searches, process hunting, the incident investigation console, and MITRE ATT&CK framework reports to hunt, analyze, and get to the root cause.
SIEM solution use cases
Explore the diverse use cases of a SIEM solution, defined based on how it serves different industries and security scenarios, to understand its versatile applications in safeguarding against cyberthreats.
- Industry-wise use cases
- Security use cases
Industry-wise use cases
| Industry | Use cases |
|---|---|
| Finance and banking |
|
| Healthcare |
|
| Government agencies |
|
| Retail and e-commerce |
|
Security use cases
1. APTs:
SIEM tools detect and mitigate sophisticated attacks, like APTs, by correlating security events with data from global threat feeds, integrating with the MITRE ATT&CK framework to identify the different phases of attacks, and enabling rapid incident response to prevent attack advancement.
2. Insider threats
A SIEM solution monitors user activities, establishes baselines of behavior, and assigns dynamic risk scores to identify insider threats, safeguarding sensitive data and critical assets from misuse or unauthorized access.
3. Malware detection
A SIEM solution analyzes network traffic and system logs to identify indicators of malware infections, enabling organizations to detect and quarantine malicious software before it causes significant damage.
4. DLP
A SIEM solution monitors data access and movement, identifies potential data exfiltration attempts, and triggers alerts or automated responses to prevent the unauthorized disclosure of sensitive information.
5. Zero-day exploits
SIEM tools help combat zero-day attacks by analyzing network behavior, identifying abnormal patterns indicative of new attack vectors, and detecting malicious sources interacting with the network by comparing them to those on global blocklists.
Explore our cyberattack libraryWhat are the benefits of a SIEM solution?
A huge time-saver for SOC teams
A SIEM solution helps you aggregate data regardless of the scale of your organization. It also streamlines security operations and automates multiple parts of the threat detection and remediation workflow, improving the mean time to resolve (MTTR) an attack.
A full-time SOC assistant available 24/7
SIEM solutions have thousands of predefined reports, alerts, and correlation rules for multiple use cases. These help SOC teams get started quickly. A SIEM solution's log search feature, investigation console, and seamless UI help you drill down to the root causes of issues without any hassles. SIEM tools offer flexibility and customization for different business requirements, from adding custom log parsing rules to constructing incident response workflows.
Adaptability according to your environment
SIEM solutions use many ML algorithms, such as clustering, regression, decision trees, and an exponential moving average, to perform UEBA, set adaptive thresholds for alerts, and triage and prioritize incidents. This truly tunes the solution according to the inflow of events, network activities, and user behavior over a period for precision and accuracy in anomaly detection.
Cost savings through compliance
A SIEM solution aids in the early detection of security breaches, minimizing the repercussions and associated business losses. In addition to this, its exhaustive library of compliance reports helps you stay audit-ready and avoid costly penalties by adhering to regulations and standards.
Security orchestration
SIEM tools integrate with other IT solutions in your network, centralizing security management.
Cyber resilience
SIEM tools help organizations quickly get back to business after a breach or security incident by offering log forensics and impact analysis and instantly generating incident reports to prevent compliance penalties.
Optimized network operations
As in security use cases, a SIEM tool proves helpful in continuously monitoring network activities and troubleshooting critical performance issues through device risk severity reports and alerts.
Evaluate SIEM using Gartner's Magic Quadrant report
The Gartner Magic Quadrant provides comparitive overview of the SIEM market by categorizing the vendors into Leaders, Challengers, Visionaries, and Niche Players. Explore the detailed report.
Download a complimentary copySIEM deployment models
SIEM functions can be completely implemented on premises, deployed through cloud-based or hybrid models, or outsourced to managed SIEM service providers. Here are the major differences between the SIEM deployment models and how businesses can choose one according to their requirements:
| Deployment model | Management | Security operations | Business suitability |
|---|---|---|---|
| On-premises |
|
Security operations are done in-house with a SOC team. | It suits large enterprises and federal agencies as they prioritize full control over data and operations and can afford the required infrastructure. |
| Cloud (SIEM as a Service) |
|
|
It suits all businesses, especially those that prioritize scaling over control and can't afford the required infrastructure for an on-premises solution. |
| Hybrid |
|
Security operations are done in-house or are outsourced. | It suits businesses transitioning from traditional on-premises setups to cloud environments. |
In addition, managed SIEM service providers help with outsourced security operations, including the configuration and management of SIEM solutions. This allows organizations to focus on their core business activities. Firms that don't require an in-house SOC team or are inexperienced in handling one prefer managed security service providers.
Check out the top SIEM tools
Here are some of the top SIEM solutions that have proved to be effective network security tools:
- Splunk
- ManageEngine Log360
- LogRhythm SIEM
- IBM Security QRadar SIEM
- OpenText ArcSight
To know more about the features offered and comparison of the SIEM solutions, read our guide on the top SIEM tools and how to choose wisely.
The future of SIEM
Hers's an overview of the evolution of SIEM solutions in terms of their technology, deployment, performance, and pricing:
- SIEM solution technology: Continuously evolving with advancements in AI and ML, future SIEM solutions will integrate advanced analytics while adapting to cloud-native architectures for enhanced scalability and flexibility.
- SIEM solution deployment: Future deployments will lean towards cloud-based solutions, which offer rapid deployment, scalability, and a reduced infrastructure overhead.
- SIEM solution performance: As data volumes continue to grow exponentially, future SIEM solutions will need to leverage distributed architectures and optimized processing techniques to deliver high-performance analytics.
- SIEM solution pricing: With the rise of subscription-based pricing models and managed SIEM services, future SIEM solutions will offer cost-effective options tailored to organizations of all sizes.
Next-gen SIEM capabilities: How have SIEM features evolved?
From log management to advanced threat analytics, SIEM tools have come a long way. To keep pace with the ever-changing security landscape, next-gen SIEM tools now provide a new set of capabilities that offers actionable intelligence to helps businesses implement proactive security strategies to improve their security postures.
SIEM summarized
FAQs and quick highlights
What does SIEM stand for?
SIEM stands for security information and event management. A SIEM solution is one of the most prominent cybersecurity tools used by enterprises to monitor networks. SIEM solutions utilize multiple risk assessment capabilities to help SOCs defend against cyberattacks.
The evolution of SIEM solutions
Here are the different stages of SIEM evolution:
- 1. SIM SIM involved the collection of all network activities. This ranged from log data collected from servers, firewalls, domain controllers, routers, databases, and NetFlow to unstructured data present in the network (such as in emails).
- 2. SEM SEM involved the analysis of the collected data. The data was analyzed using various techniques, alerts about security events were sent, and workflows were initiated to respond to any abnormal behaviors.
- 3. Next-gen SIEM As cyberthreats evolved and became more sophisticated, the need for more advanced SIEM solutions was made evident. Next-gen SIEM solutions build upon traditional SIEM solutions by integrating advanced analytics, UEBA, and orchestration capabilities. This allows for more proactive threat hunting, better anomaly detection, and faster incident response times.
What are the primary features of a SIEM tool?
The primary features of a SIEM solution include the following:
- End-to-end log management
- Event correlation
- UEBA
- Reporting and alerting
- Advanced threat analytics
- An incident management and response console
- Log searching and forensics
SIEM vs. SOAR
SIEM solutions centralize log data for analysis and security incident detection. SOAR helps with:
- Automating incident response actions.
- Integrating with security tools for orchestrated responses.
- Executing playbooks.
- Improving the efficiency of security operations.
Here are some related sources
- Ebooks
- Whitepapers
- Case Studies
Are you looking for a SIEM solution?
Explore Log360, ManageEngine's SIEM solution:
About Log360
Log360 is a unified SIEM solution with integrated DLP and CASB capabilities that detects, prioritizes, investigates and responds to security threats. Vigil IQ, the solution's TDIR module, combines threat intelligence, an analytical Incident Workbench, ML-based anomaly detection and rule-based attack detection techniques to detect sophisticated attacks, and it offers an incident management console for effectively remediating detected threats. Log360 provides holistic security visibility across on-premises, cloud and hybrid networks with its intuitive and advanced security analytics and monitoring capabilities. For more information about Log360, visit manageengine.com/log-management/ and follow the LinkedIn page for regular updates.
Connect with our experts for a personalized demo:
Talk to our experts
Find out if Log360 is the right fit for you by scheduling a demo session with us. Our experts will walk you through the solution.
Download and explore the solution in your environment:
Try a free, 30-day trial of Log360
Try out Log360 yourself by downloading a free, 30-day, fully functional trial with no restrictions.
Find the perfect plan for your business
Annual price starts at $2,130To assist your evaluation we offer:
- 30-day, fully functional free trial
- No user limits
- Free 24/5 tech support
Thanks for your interest in ManageEngine Log30
We have received your request for a personalized demo and will contact you shortly.
Fill this form to schedule a personalized web demo
- What is SIEM
- Understanding SIEM
- SIEM features and working
- SIEM usecases
- SIEM deployment
- Future of SIEM
- Explore a SIEM tool


