Enterprise networks are no longer contained to corporate premises. The attack surface has expanded with perimeterless networks, and it has become easier to access vulnerable entry points. In such a landscape, with threat actors executing increasingly complex attacks to get hold of critical data and resources, a powerful network security monitoring tool like ManageEngine EventLog Analyzer is required.
Aided by its ML and AI capabilities, EventLog Analyzer monitors, records, and analyzes network events. Enterprises can benefit from useful log reports, real-time alerts, internal and external threat detection, threat prevention, and automated incident response.
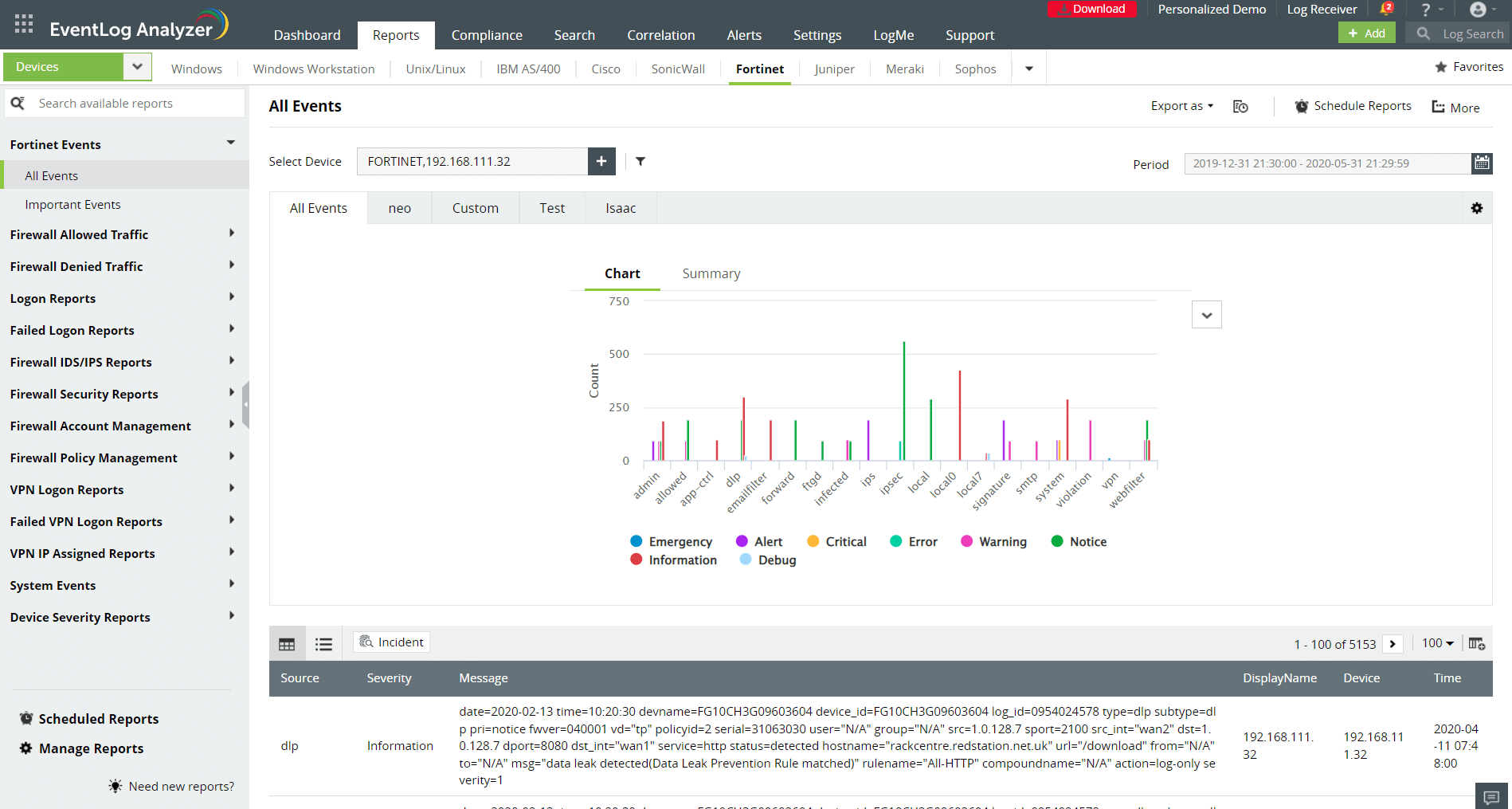
EventLog Analyzer ensures network perimeter security by automatically collecting and monitoring log data from a diverse set of network devices and endpoint security solutions. The tool records, analyzes, and correlates the logs to help you gain a holistic picture of your network traffic patterns with hundreds of predefined reports on:

EventLog Analyzer ensures network perimeter security by automatically collecting and monitoring log data from a diverse set of network devices and endpoint security solutions. The tool records, analyzes, and correlates the logs to help you gain a holistic picture of your network traffic patterns with hundreds of predefined reports on:
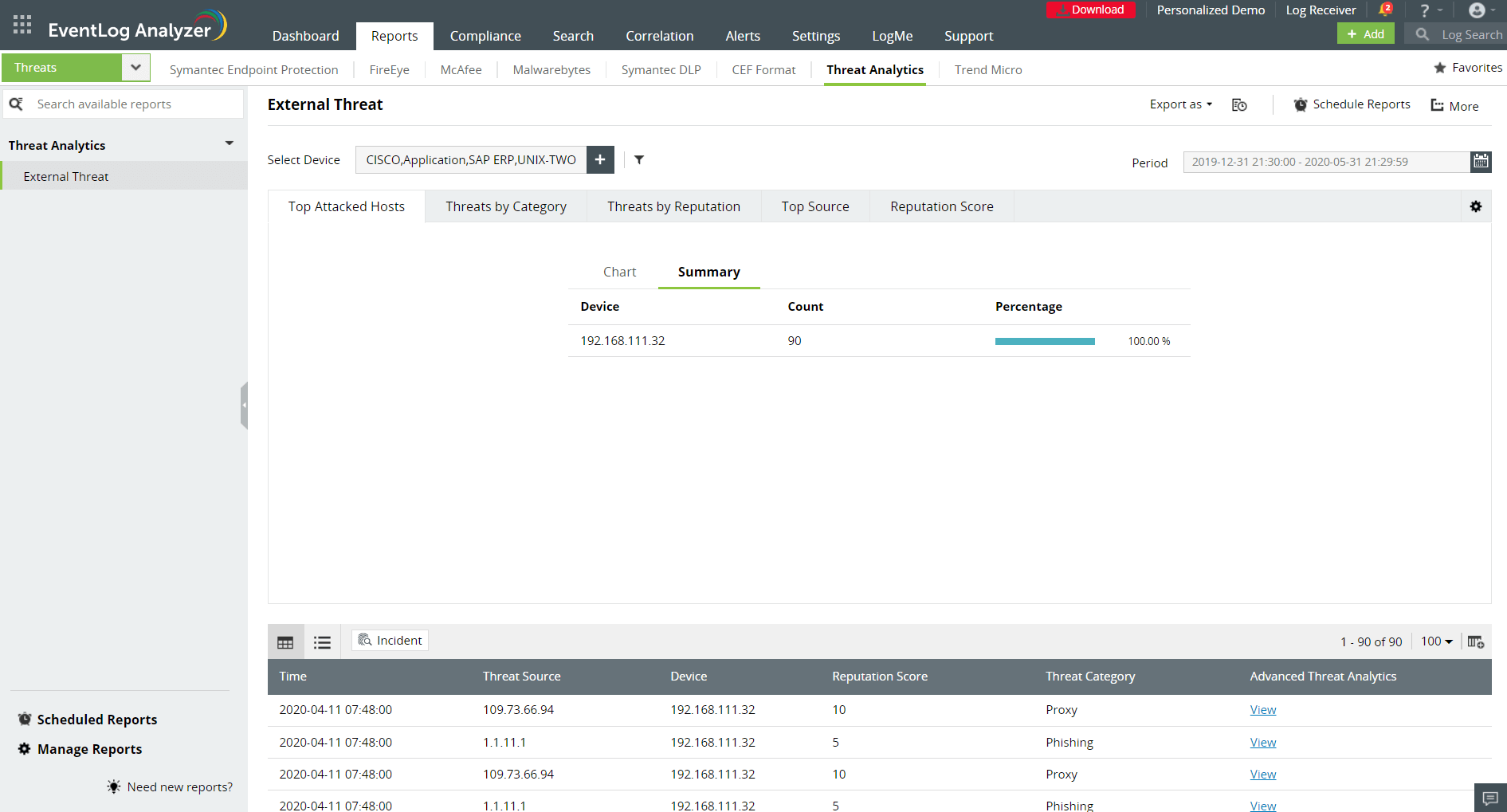
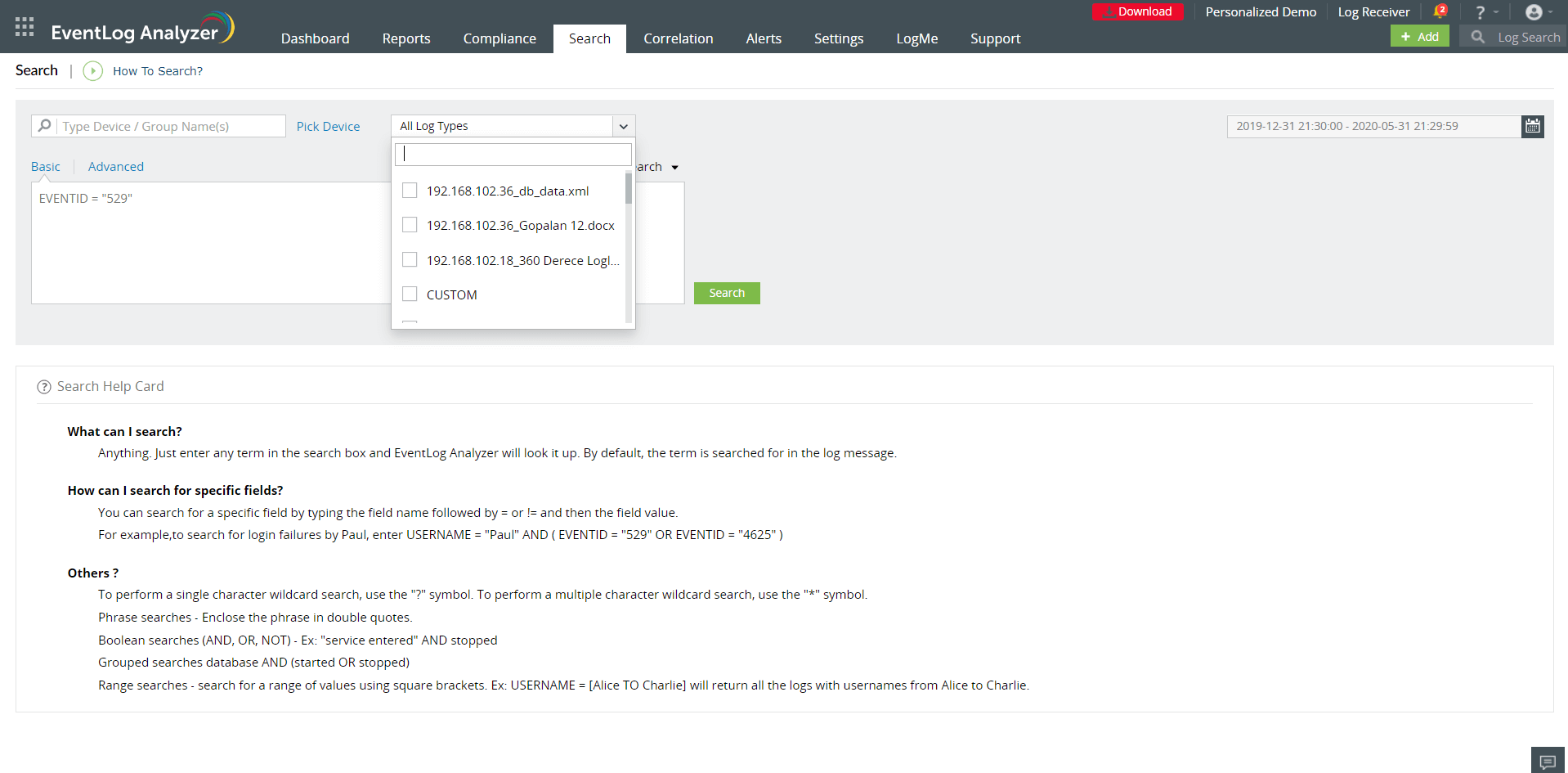
Use EventLog Analyzer's powerful log search engine to retrace security incidents, reconstruct the crime scene, and conduct thorough forensic analysis. The flexible search functionality allows you to use the event ID, event severity, source, username, IP address, and other key details to construct a wide range of search strings with phrases, Boolean operators, wildcards, and more. You can also combine multiple query results and apply filters to conduct root cause analysis with the advanced search feature. The reports on archived log data generated in this process can be used as evidence in legal proceedings.
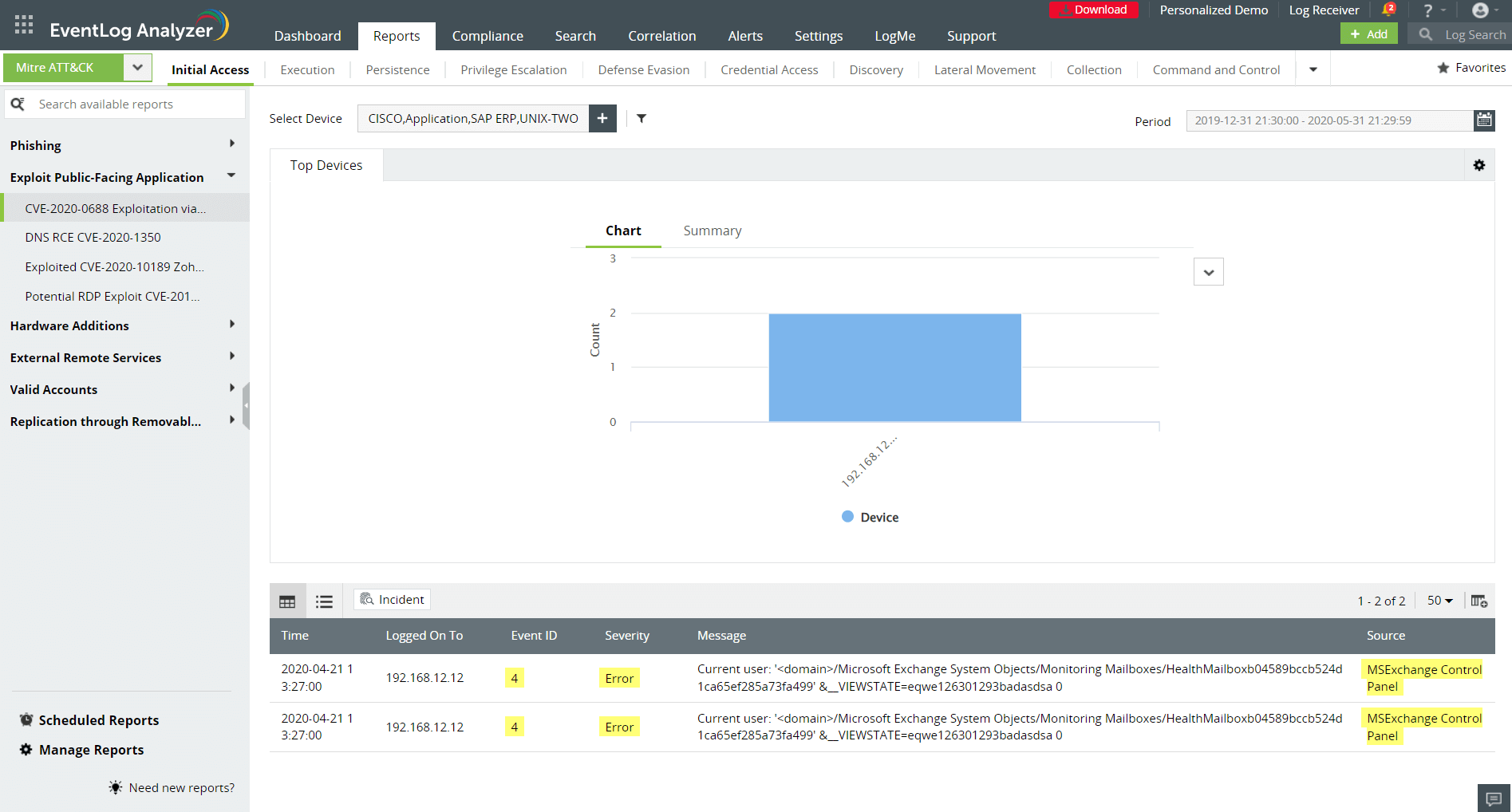
Forestall critical threats by correlating events across your network with the help of over 30 predefined correlation rules and a custom rule builder. EventLog Analyzer is also integrated with the MITRE ATT&CK® framework, which maps the detected anomalies, like privilege escalation, defense evasion, and credential access, to the possible objectives of threat actors before a full-blown attack is launched. View the chronological sequence of security incidents and set up email and SMS alerts.
Automate responses to security incidents with EventLog Analyzer's predefined workflows. Take proactive measures, like locking, quarantining, and disabling systems and user accounts that get hacked. Customize incident workflows, alter the active status, make changes to the sequence, and view reports on workflow execution by accessing the central workflow management page.

With EventLog Analyzer's in-depth Sysmon log analysis capability, monitor network connections and get visibility into each connection’s process ID, source IP address, source and destination ports, and more. You can also analyze logs generated when a process executes a DNS query, regardless of its result (Success, Failure, or Cached).
Detect and mitigate threats from internal and external actors with real-time user session tracking. The user audit trail reports help with network security monitoring activities by providing exhaustive details on the user logon trends, audit policy changes, objects accessed, and user account changes.
Learn moreSet up real-time alerts for suspicious activities in your network. EventLog Analyzer equips you with over 500 predefined alert profiles for the most common events, like firewall flood attacks, authentication policy rights being granted or revoked, and admin resource access attempts. Prioritize the alerts and get real-time notifications through SMS and email.
Learn moreIdentify and respond to threat indicators instantly with an effective incident management system in place. Raise tickets for critical alerts and assign them to the relevant admins through EventLog Analyzer's console or by integrating the tool with your organization's help desk software.
Detect over 600 million malicious sources and differentiate actual threat patterns from the huge number of false positives firing across enterprise networks with EventLog Analyzer's threat intelligence solution.
The correlation engine analyzes millions of logs effectively to provide you with a larger picture of related events that might seem innocuous individually. Attack patterns of web server threats, ransomware, file integrity threats, unauthorized crypto mining, and other critical attacks are detected with EventLog Analyzer's powerful correlation techniques.
Enterprise networks have grown more distributed and complex due to the rise of hybrid working models and the migration of business operations to cloud environments. Installing just perimeter security solutions will only create a basic layer of defense. Systems, servers, and other network entities generate logs that record all network activities. A centralized log management system like ManageEngine EventLog Analyzer helps you automate the monitoring of your network logs; obtain a comprehensive view of network performance, persisting issues, and vulnerabilities; and prevent attacks.
Network security tools employ strategies to defend the network, prevent attacks, and respond to security emergencies with features such as network device monitoring, application log management, real-time event correlation, log forensics, and threat mitigation. Integrating dynamic threat detection approaches and automating tasks in the cybersecurity workflow, like network scanning, log collection, and report generation, are paramount to a state-of-the-art network security solution.
Network security tools help security professionals automate the daunting task of analyzing huge volumes of log data. ManageEngine EventLog Analyzer processes over 20,000 logs per second, produces real-time reports on network events, helps professionals configure custom alerts, and automates responses to counter network intrusions.
your network security activities with EventLog Analyzer.
Download now