Security information and event management (SIEM) solutions provide a holistic view of all the activities that happen in an IT infrastructure by monitoring network activities, and employing threat intelligence and user and entity behavior analytics (UEBA) to detect and mitigate attacks.
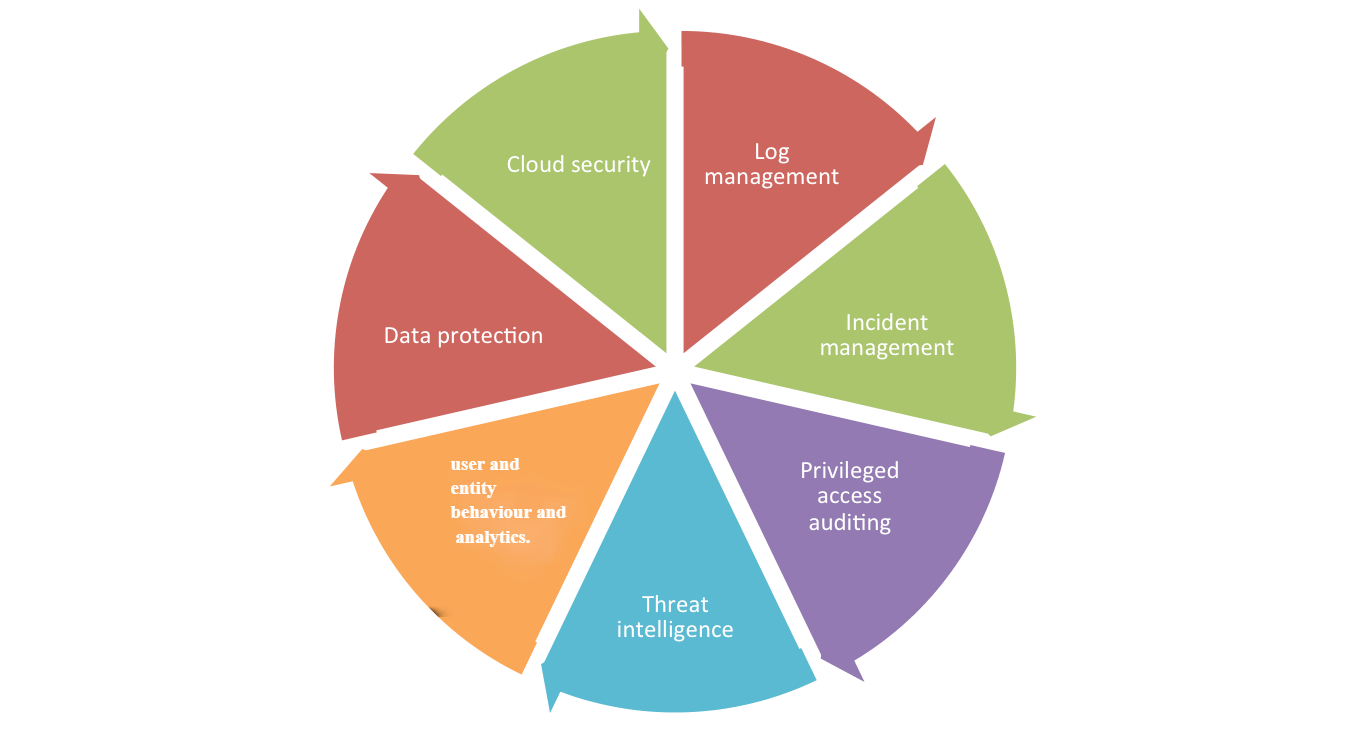
Log management involves the collection, normalization, and analysis of log data, and is used to gain better visibility into network activities, detect attacks and security incidents, and meet the requirements of IT regulatory mandates. For effective log analysis, SIEM solutions employ different processes such as log correlation and forensics, which help detect data breaches and attacks in real time. Log management also includes securely archiving log data to retain logs for a custom time period.
A security incident is an event that is abnormal from regular activities in a network. An incident is capable of putting the sensitive data of an organization at risk and can lead to a data breach or an attack, but not always. Incident management includes detecting and mitigating security incidents.
Incident detection is the process of identifying a security threat happening on a network. You can detect incidents using various techniques like log correlation, UEBA, and threat analytics.
Incident resolution refers to solving an incident or an attack in the network and getting the network back to a functional state. SIEM solutions provide various workflows that can be automatically executed when an alert is triggered. These workflows help a great deal in preventing attacks from spreading laterally within the network
Privileged user accounts are those with administrator privileges. These privileges can permit the user to install, remove, or update software; modify system configurations; create, modify, or change user permissions; and more.
Privileged accounts are of paramount importance to ensure network safety, as just one compromised privileged user account could give an attacker more access to network resources. It's essential to track and audit the actions of privileged users, and generate real-time alerts for abnormal activities. Monitoring privileged user accounts can help track and prevent insider attacks, as these accounts have permission to observe the activities of other users in a network. If users try to escalate their privileges, it could be a potential threat. SIEM solutions can detect such behavior and audit privileged users' activities to enhance network security.
Threat intelligence is essential for preventing an attack from occurring rather than reacting to the incident after it happens. Threat intelligence combines the knowledge gained from evidence, contextual information, indicators, and action responses collected from various threats, and produces concrete instances of indicators of compromise (IOCs). It can also provide information about the tactics, techniques, and procedures (TTPs) involved in the emerging threats, and can monitor current network activities to spot anomalous patterns. Threat intelligence incorporates artificial intelligence (AI) and machine learning (ML) tools to distinguish regular and irregular patterns in a network to determine if an activity poses a threat to the network.
Cloud security involves the protection of data and infrastructure hosted on cloud platforms. Cloud platforms are equally vulnerable as on-premises platforms when it comes to security. SIEM solutions help IT security admins secure cloud platforms by detecting network anomalies, abnormal user behaviors, unauthorized access to critical resources, and more.
UEBA in SIEM solutions is usually based on ML or AI, and analyzes the normal work pattern of a user, or the typical way a particular user accesses the network on an everyday basis. It can detect deviations from normal behavior, raise an alert, and notify the security administrator immediately.
The more information the SIEM solution processes from different sources like routers, firewalls, domain controllers, applications, databases, and any computational device in a network, the more precise the anomaly detection can become over time. UEBA uses ML techniques and AI algorithms to process the information, learn the patterns of threats, and identify if a particular pattern in a network is similar to a threat anomaly that has previously taken place. With this detection, UEBA helps generate real-time alerts and leverages automation in threat prevention to make it more reliable.
One of the primary goals of security professionals is to prevent sensitive data loss or exfiltration. SIEM solutions help detect, mitigate, and prevent data breaches by continuously monitoring user behavior. SIEM solutions track accesses to critical data and identify unauthorized accesses or access attempts. It also watches out for privilege escalations in user accounts, and any changes to data made by those accounts. When these detection capabilities are combined with workflow management, security admins can configure the SIEM solution to prevent malicious activities in the network.
Zoho Corporation Pvt. Ltd. All rights reserved.