Become more cyber resilient by automating threat detection and response with Log360, a comprehensive SIEM solution.
When an organization's IT infrastructure grows rapidly, manually monitoring security events for hundreds of devices on a daily basis becomes very challenging. Security automation refers to detection, investigation, and remediation of cyber incidents with minimal human intervention. The longer it takes to detect and remediate cyberthreats, the more expensive it is for the organization to recover from the attack. Manual processes slow down threat detection and mitigation, cause alert fatigue, and lead to errors in configurations, leaving the network more vulnerable to cyberattacks.
Using security automation, organizations can reduce the time taken to respond to security incidents and significantly reduce the costs associated with a data breach. It also boosts the efficiency of the security team by reducing the security administrator's workload, allowing them to spend their valuable time on more important tasks.
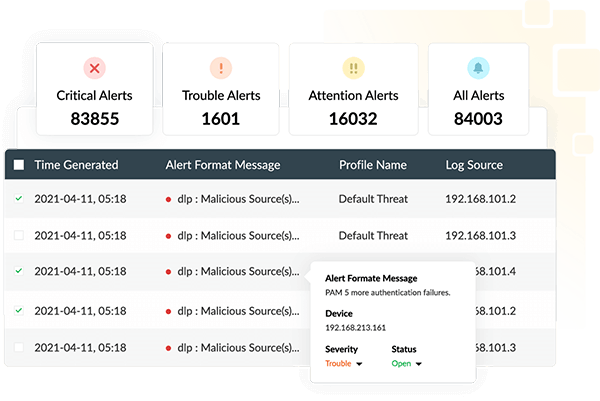
Log360's real-time alerting system will notify you instantly when any security threat is detected in the organization network. It includes over 1,000 predefined alert criteria that address a wide range of cybersecurity use cases. You can configure alert profiles to detect indicators of compromise (IoC) and notify you via email or SMS when a security incident occurs.
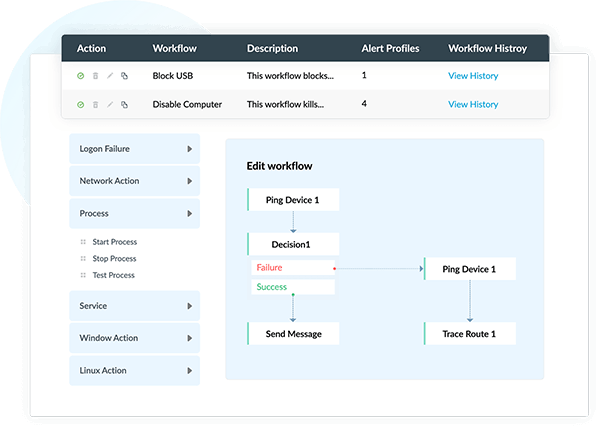
Using Log360's incident response workflows, you can automate the sequence of steps to be taken immediately when a security incident occurs in the network. Apart from using built-in workflows, you can also customize workflows as per your requirements using the flexible drag-and-drop interface. With Log360, you can build workflows to disable compromised user accounts, add inbound and outbound firewall rules, terminate processes running on affected devices, and more.
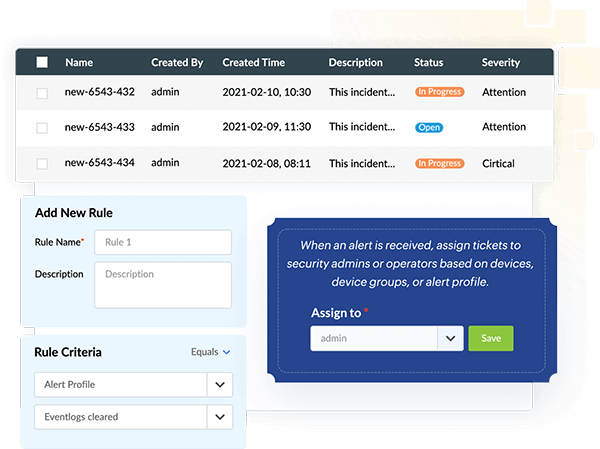
With Log360, you can resolve security incidents by assigning tickets to technicians and tracking the status of each ticket with the help of a built-in ticketing system. Every time an alert is raised, a ticket will be automatically assigned to the appropriate security administrator.
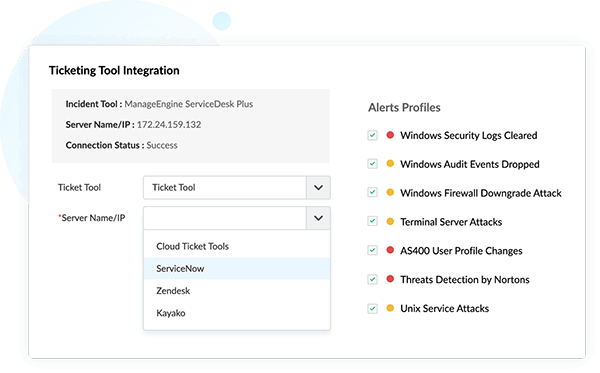
Apart from resolving security incidents using Log360's built-in ticketing system, you can also integrate Log360 with some major help desk tools such as:

Comply with various IT regulations such as the GDPR, PCI DSS, HIPAA, ISO 27001, NIST and more using Log360's built-in, audit-ready reports and compliance violation alerts. The reports are generated automatically, and you can customize them as per your policy requirements.
By obtaining threat information from various threat intelligence solutions, Log360 can automatically generate reports and alerts when any security threat is detected in the organization network.
Threat intelligence solutions supported by Log360 include FireEye Threat Solutions, Symantec Endpoint Solutions, Symantec DLP Applications, and Malwarebytes Solutions.
Log360 can detect the latest attack patterns in the cybersecurity landscape by utilizing the MITRE ATT&CK framework. It automatically generates alerts and detailed reports about any threat that follows an attack technique mentioned in the ATT&CK knowledge base.