Cybersecurity is a power game. Cybercriminals and enterprises are in a continuous tug of war, with privileged information as the coveted prize. While enterprises fight to protect sensitive data, cybercriminals fight to gain access to it. Each side chooses a weapon of their choice. In this blog we will explore a weapon that is a popular choice for both sides: PowerShell.
Contents:
To call Windows PowerShell a command line interpreter would be undermining its capabilities. While it can do everything a shell program like Command Prompt can do, PowerShell is also a scripting language used by administrators to automate tasks. A good example is Active Directory management. Administrators can spend hours manually managing their organization's Active Directory, or they can use a single PowerShell script or command to carry out bulk actions. A lot of administrators prefer PowerShell to the GUI tools they can use like AD Administrative Center or AD Users and Computers.
 Fig. 1: A PowerShell window
Fig. 1: A PowerShell window
PowerShell scripting is a vast subject. To better understand the concepts discussed throughout this blog, let us explore three important components of PowerShell scripting.
While PowerShell is an administrator's favorite tool, it also a hacker's go-to attack vector. This is because of PowerShell's traceability, or lack thereof, in a Windows environment. Since PowerShell is an allowlisted tool, it is easier for cybercriminals to escalate their privileges and execute malicious scripts.
PowerShell is mostly used as a post-exploitation tool. This is because PowerShell is enabled by default in most user accounts. Once a hacker enters the network, they can run the program as an administrator or easily use a couple of commands to escalate privileges. Let us explore five ways cybercriminals can use PowerShell to execute cyberattacks.
PowerShell scripting: According to the MITRE ATT&CK® framework, PowerShell is listed as a sub-technique under Command and Scripting interpreter. Cybercriminals often abuse PowerShell cmdlets to get information about their targets and execute malicious code remotely. PowerShell is also used to download and execute malware files in the computer's memory without actually touching the disk. Some PowerShell cmdlets used to carry out cyberattacks include Invoke-Command or Start-Process. Invoke-Command is used to execute a command remotely and Start-Process is used to run an
Domain discovery: Once the attackers have penetrated the enterprise network, they can use certain cmdlets to get a list of existing domains, groups, and the user or computer accounts in these domains as a local administrator. This helps them determine their next target based on the privileges these accounts or groups may have. In a Windows environment, some of the cmdlets they can use include Get-ADDomain to get a list of domains in the directory, Get-ADUser to get a list of users, Get-ADComputer to get a list of computers in the directory, and Get-ADGroupMember to get a list of users in a particular group. These cmdlets give a good deal of information about each of the objects, especially Get-ADComputer, which gives in-depth information about each host.
Privilege escalation: Access to PowerShell means the ability to easily escalate privileges. As seen earlier, once the attacker, posing as a local administrator, gets information about the list of computers in the domain and has picked a target, they will check the Get-Acl cmdlet to check the ACL for their target.
Once they get a list of permissions, the attackers will choose the user or user group that has higher permissions to the target computer. They will get information about the members who belong to that group (using the Get-ADGroupMember cmdlet). They will then go through the list of group members to check if any of the accounts match those they've obtained access to. Once they do, they will use the PS-Exec command to remotely execute scripts in their target machine using the current system.
Lateral movement: Lateral movement is an attack technique that involves the attacker moving from one compromised host to another in the network. Usually, lateral movement involves using one of two tools: Windows Remote Management (WinRM) or Cobalt Strike. WinRM is a built-in tool in all Windows machines used to establish remote connections, and Cobalt Strike is a pen-testing tool used to simulate attacks.
There are two ways to use PowerShell for lateral movement:
Windows offers three kinds of logging mechanisms to track PowerShell activity.
PowerShell logging can be enabled through the local Group Policy Editor for one specific machine or through the Group Policy Management Editor for a user group or OU in a domain. Let's see how to do this in six simple steps:
Open Group Policy Management Editor.
 Fig. 2: Group Policy Management Editor
Fig. 2: Group Policy Management Editor
Click Administrative Templates under User Configuration or Computer Configuration, based on the requirement.
Click Windows Components.
Scroll down and click Windows PowerShell.
Select the PowerShell logging mechanisms that need to be enabled out of those present. Let's say you want to enable script block logs.
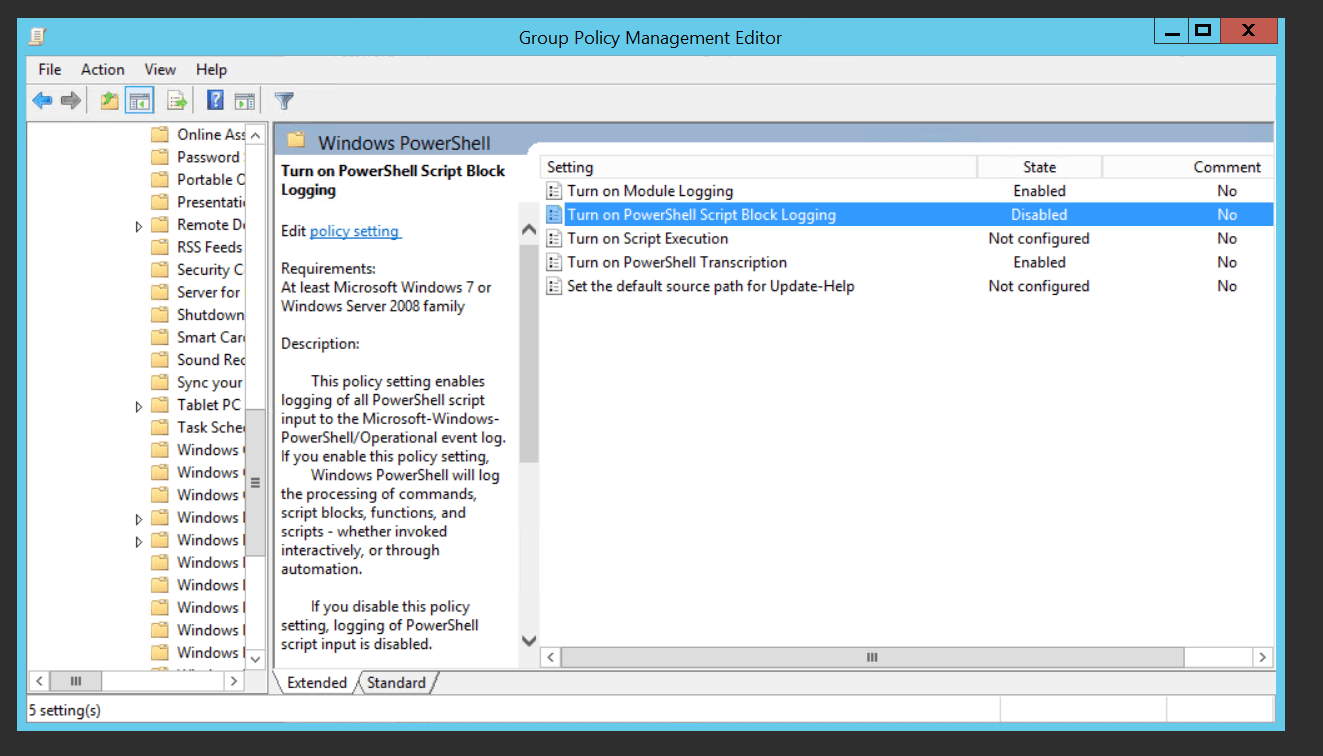
Click Turn on PowerShell Script Block Logging. Select Enabled from the given radio buttons, and click Apply.
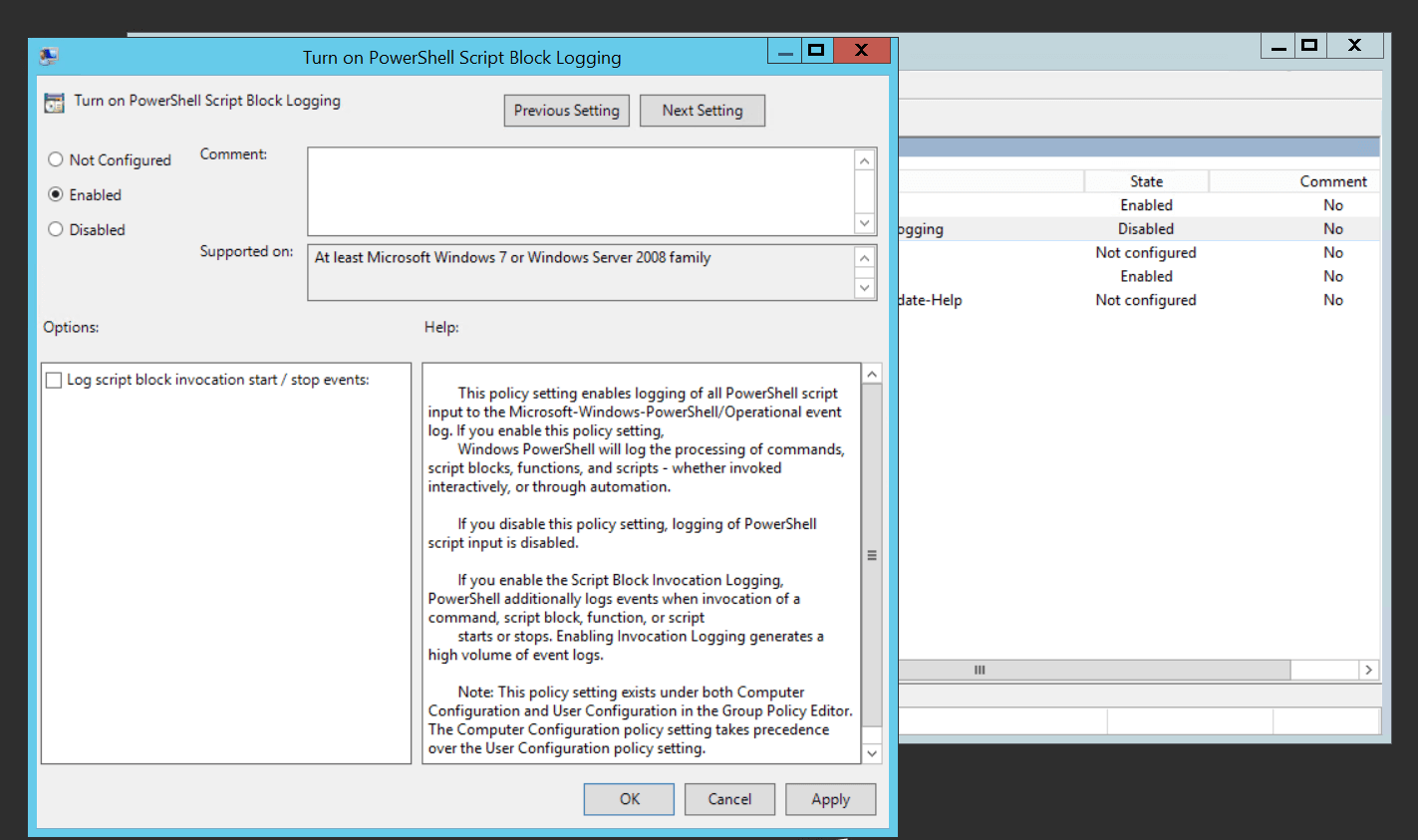
A similar process can be used to enable the generation of other PowerShell logs. A lot of organizations disable PowerShell logging because of the large number of event logs that are generated. As a cybersecurity best practice, it is recommended that organizations enable PowerShell logging—if not all three types, then at least script block logging.
It can be difficult for IT administrators to keep track of the many event logs generated to track PowerShell scripts. A SIEM solution like Log360, which has an Active Directory auditing functionality, can help IT admins make the process easier in the following ways:
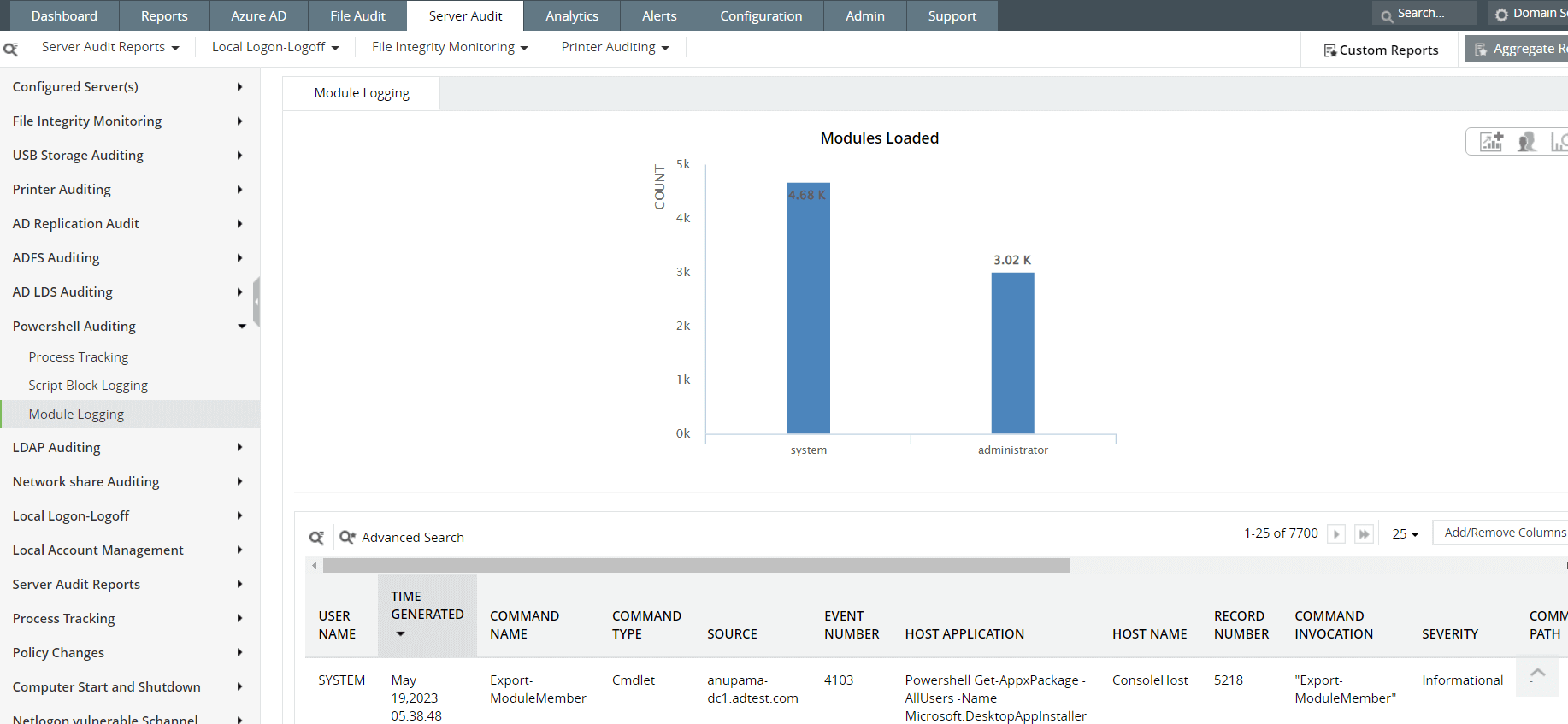 Fig. 3: Module logging reports in ManageEngine Log360
Fig. 3: Module logging reports in ManageEngine Log360
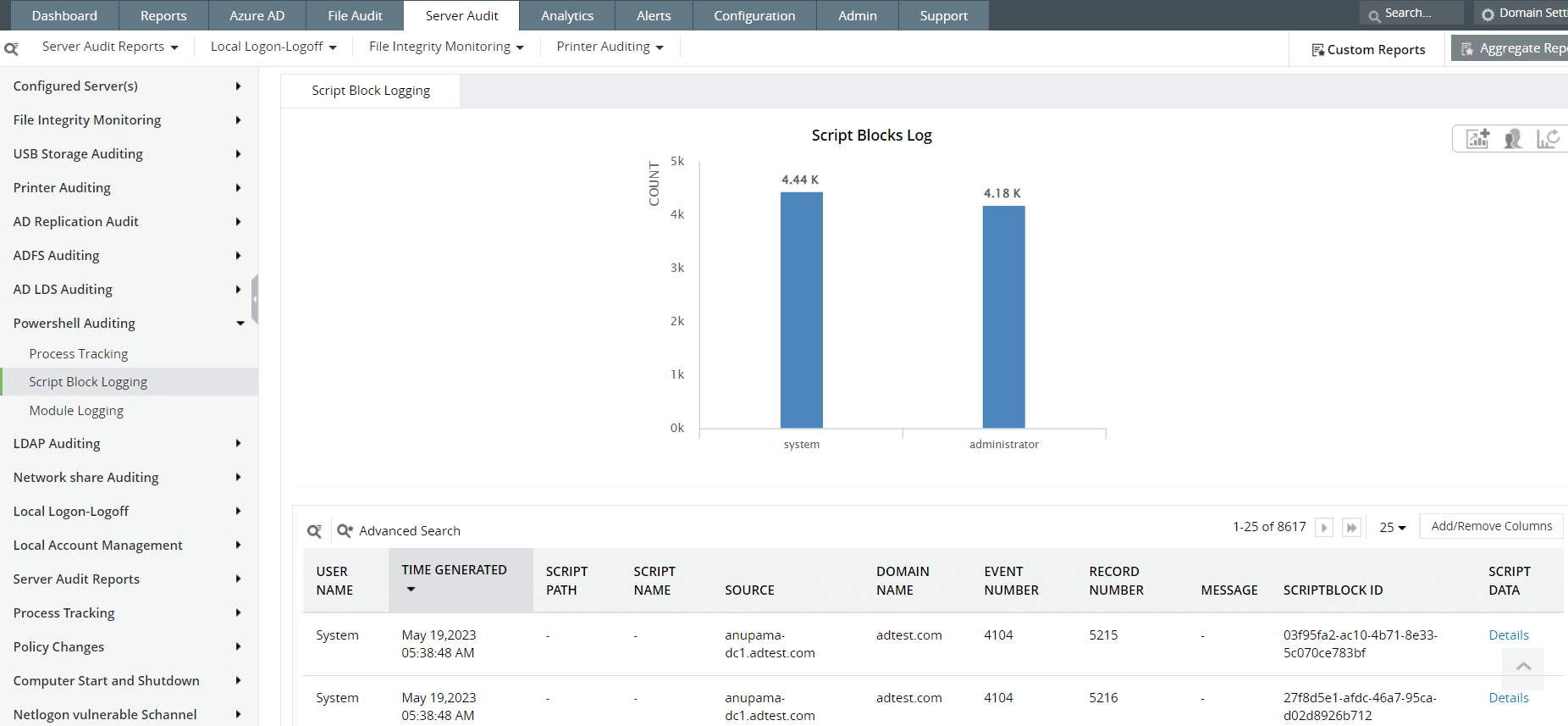 Fig. 4: Script Block Logging reports in ManageEngine Log360
Fig. 4: Script Block Logging reports in ManageEngine Log360
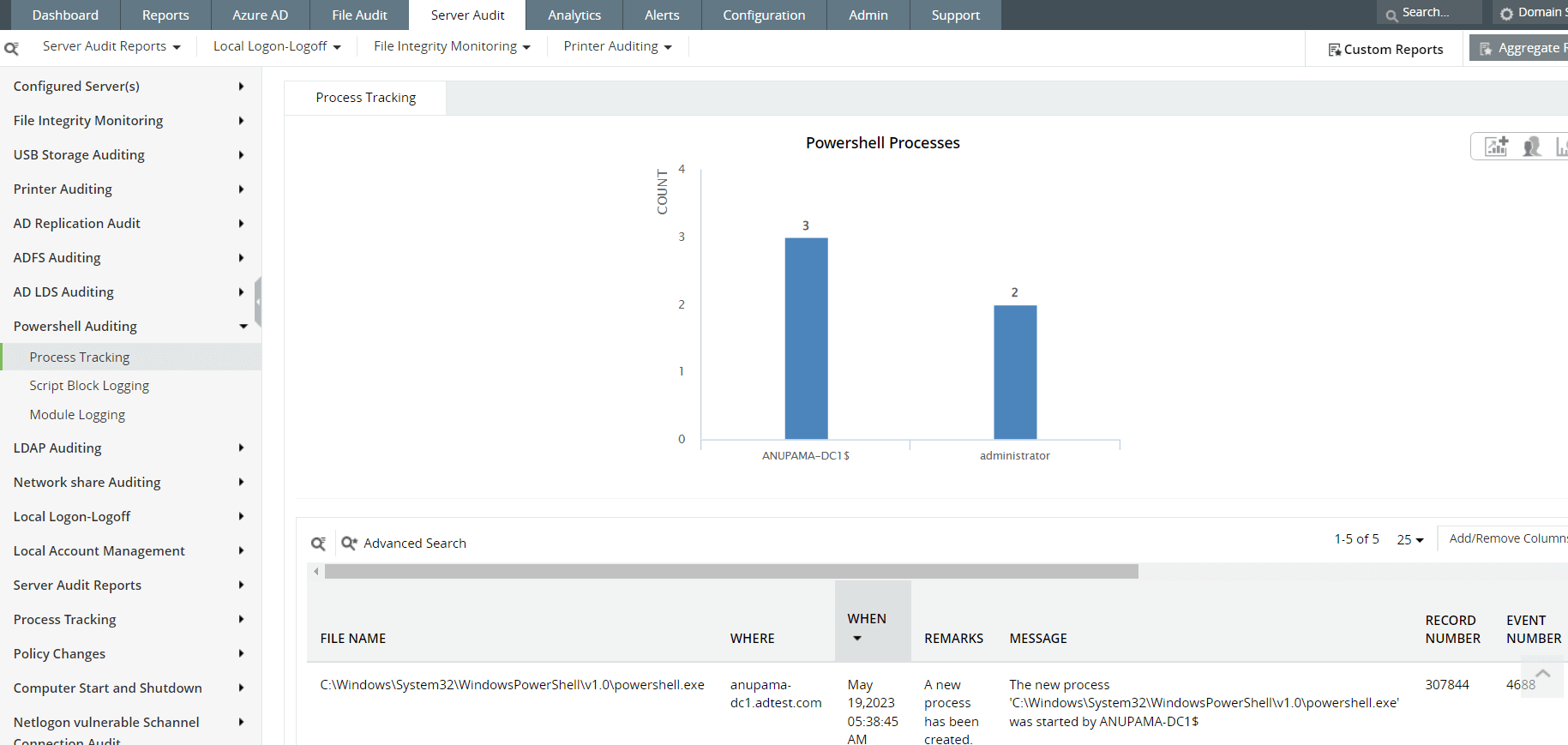 Fig. 5: PowerShell process tracking reports in ManageEngine Log360
Fig. 5: PowerShell process tracking reports in ManageEngine Log360
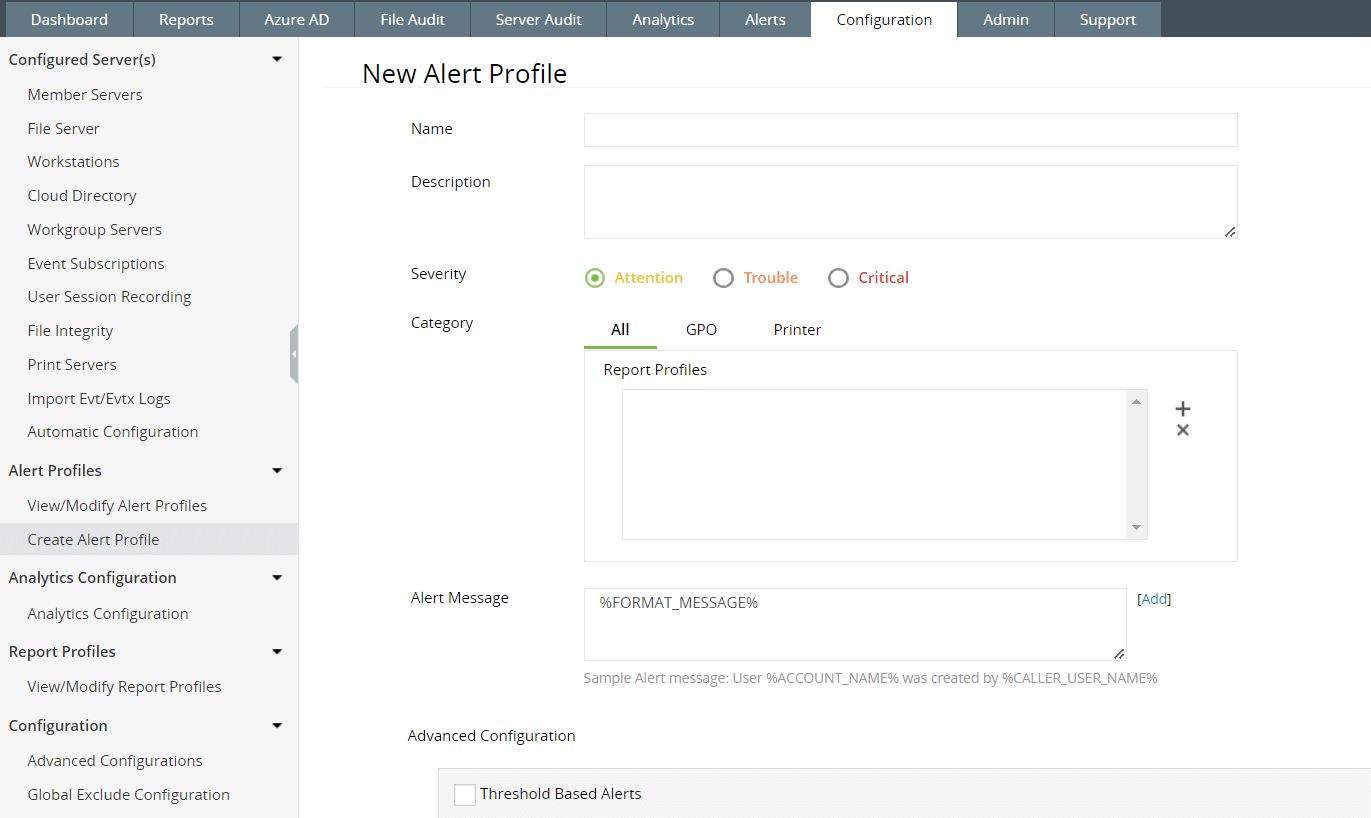 Fig. 6: Alert Profile configuration feature in ManageEngine Log360
Fig. 6: Alert Profile configuration feature in ManageEngine Log360
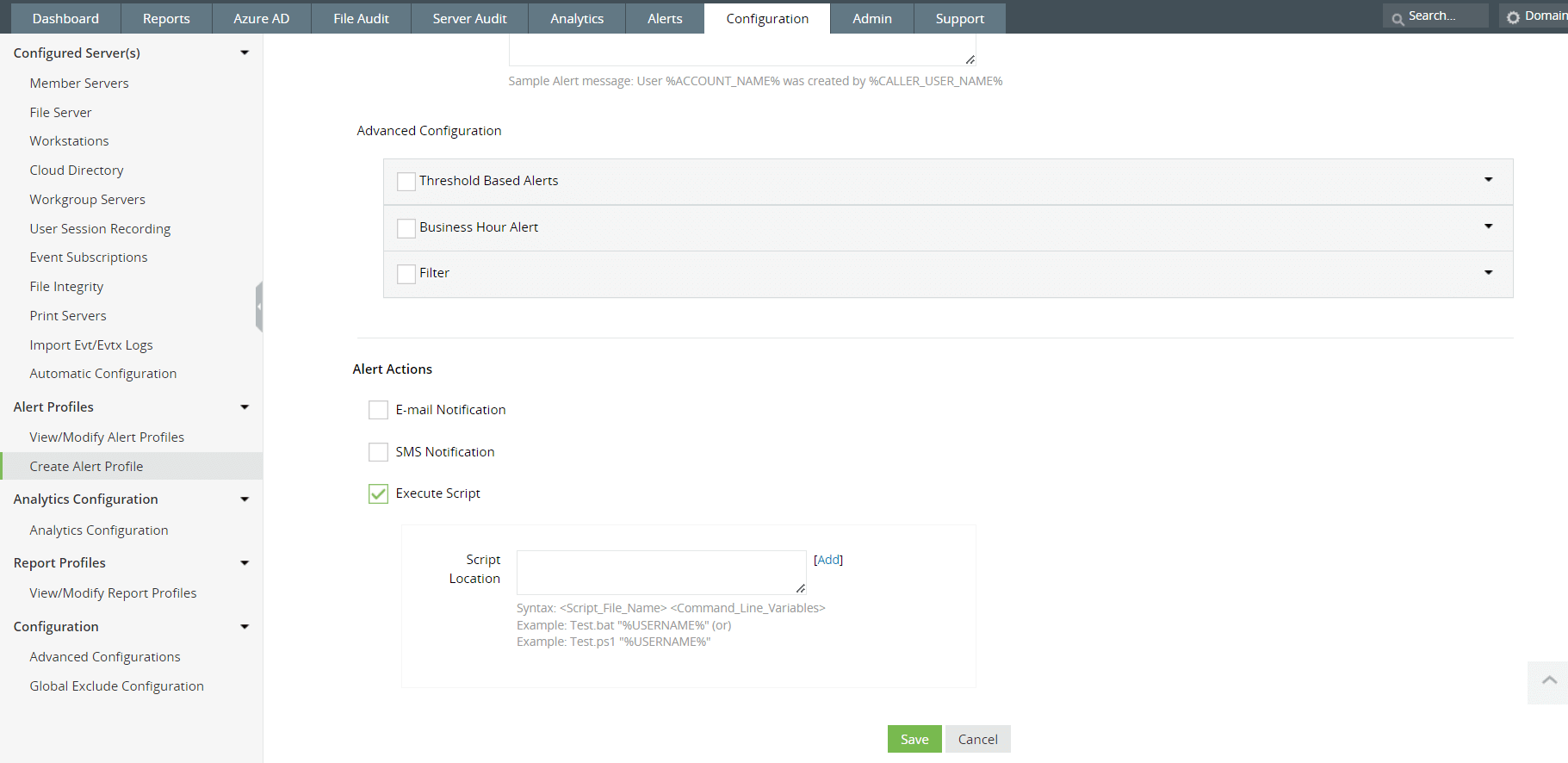 Fig. 7: Execute Script feature in ManageEngine Log360
Fig. 7: Execute Script feature in ManageEngine Log360
To learn more about PowerShell auditing using Log360, reach out to our product experts for a personalized demo or download a 30-day, free trial to check it out for yourself.
You will receive regular updates on the latest news on cybersecurity.
© 2021 Zoho Corporation Pvt. Ltd. All rights reserved.