Managing mobile devices such as smartphones, laptops, and tablets has become an integral part of supporting today's increasingly distributed workforce. The rapid transition to remote work, coupled with the ever-expanding BYOD culture among organizations, has hugely increased the strain on IT teams; they must simultaneously manage myriad connected devices for smooth business operations and ensure that security is just as intact outside the corporate perimeter. Furthermore, a lot of sensitive corporate information resides on and is exchanged between employee-owned devices.
For smoother management of such mobile devices within the network, IT security teams deploy what is called a mobile device management (MDM) solution. This type of tool facilitates a policy-driven approach to securing, monitoring, and managing end-user mobile devices, providing complete network visibility and security while allowing users to work with their own devices efficiently.
MDM systems help IT teams remotely manage mobile devices within the corporate network by streamlining operations such as controlling device configurations, distributing and monitoring applications, and mitigating vulnerabilities. However, merely managing these devices doesn't address the security challenges posed by a distributed workforce. A sound authentication system is imperative to establish trust and ensure full-on mobile ecosystem security.
A vast majority of IT security professionals agree that passwords don't provide the best means of authentication because of the obvious difficulties that come with password usage—the need for frequent resets, the sharing of passwords in clear-text among employees, etc. Furthermore, passwords verify the identify of just the individual, whereas a more robust authentication system verifies the identity of both users and devices to ensure complete trust and security.
Digital certificates that rely on public key encryption provide a more effective authentication mechanism. When the private key paired with a certificate is mapped to a particular device, it cannot be duplicated in another device, ensuring only authorized devices can access corporate resources. This is often used in combination with user identification mechanisms such as biometrics or PINs to eliminate the possibility of unauthorized access.
Another advantage of deploying digital certificates to mobile devices is the flexibility of having a single credential to authenticate a wide variety of enterprise applications. Certificate-based authentication on mobile devices facilitates:
Given the advantages brought by certificate authentication on mobile devices, leading MDM solutions offer discovery and management of device certificates as one of their key workflows. However, for a seamless user experience and uninterrupted access, enterprise IT teams need a more efficient technique to automate the life cycle management of certificates stored in their MDM solutions.
One way to achieve this is to integrate the MDM solution with a digital certificate management solution. In this approach, the MDM solution acts as the broker between the mobile device and the certificate management platform that effectively automates the life cycle management of certificates deployed to mobile devices.
Key Manager Plus, through its integration with ManageEngine’s comprehensive MDM solution Mobile Device Manager Plus, facilitates end-to-end life cycle management of digital certificates deployed to mobile devices across the corporate network. Listed below are some of the certificate management operations that can be performed on certificates deployed to mobile devices.
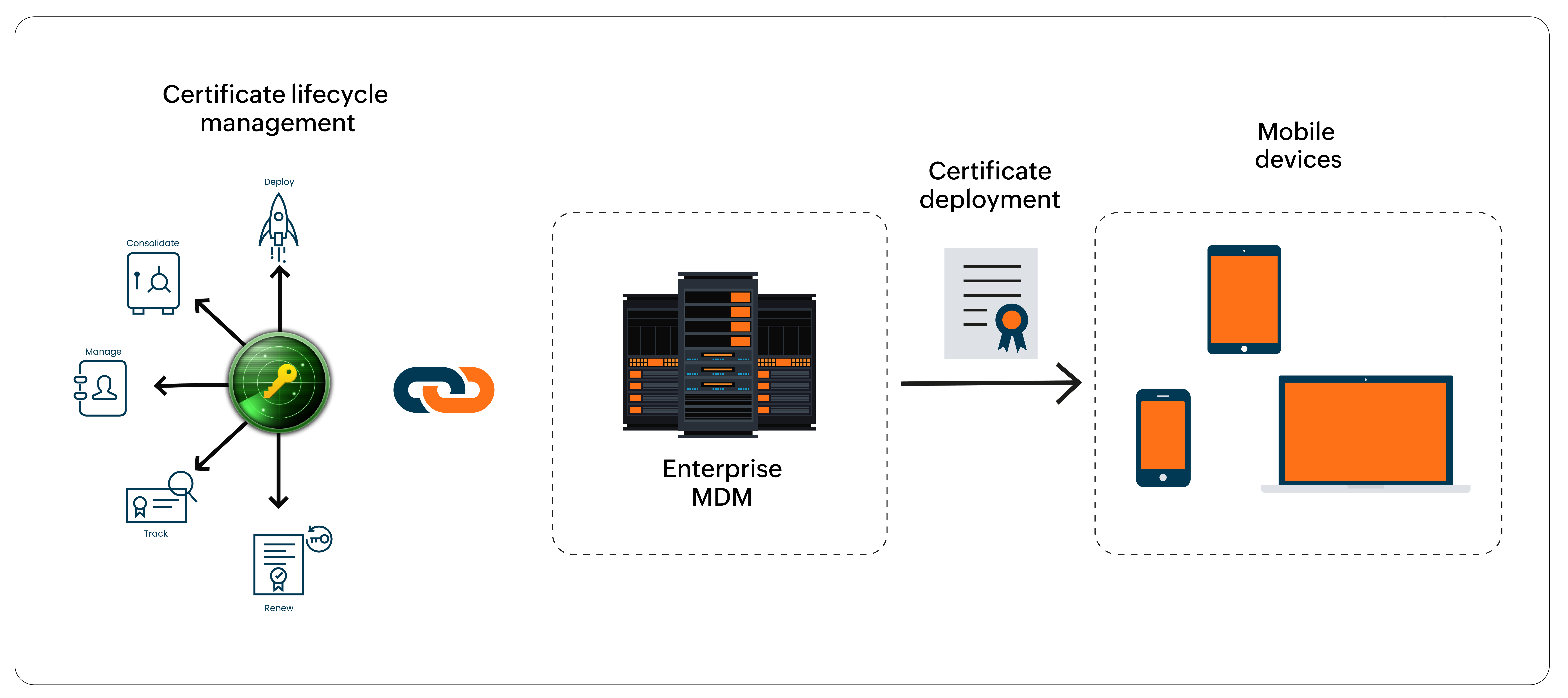
Key Manager Plus establishes a secure API connection with the Mobile Device Manager Plus server and discovers the certificates that are deployed to mobile devices within the network through Mobile Device Manager Plus.
The certificates discovered from Mobile Device Manager Plus can then be imported into Key Manager Plus' centralized certificate repository. Admins can deploy certificates to specific mobile device platforms directly from the certificate repository.
Key Manager Plus continuously monitors the validity of certificates deployed to mobile devices and sends automated alerts to administrators when a certificate is about to expire. The notification window for these alerts can be customized. This enables IT administrators to attain complete visibility and control over mobile device certificates, facilitating uninterrupted connections to corporate assets for legitimate access requests.
Key Manager Plus enables IT administrators to generate on-demand or scheduled reports on mobile device certificates to effectively track the usage of certificates deployed to devices across the network. Reports can be filtered according to the date of import or the OS platform and can also be exported as PDF or CSV files and sent to specific recipients for further action.

Key Manager Plus is integrated with ManageEngine’s Password Manager Pro, to provide unified privileged identity management platform.

ManageEngine’s Key Manager Plus enables us to stay on top of SSL certificates for all of our websites. With Key Manager Plus, we’re able to monitor which certificates are nearing expiration and roll out new certificates in a timely manner.Ken Odibe Senior cloud infrastructure consultant, Sapphire systems.
