Combating threats with UEBA: Cyberattacks in the education sector
In this four-part series, we explore hypothetical cyberattacks inspired by real-life events in four different industries: healthcare, finance, manufacturing, and education. We'll take a look at unforeseen security attack scenarios, and discover how user and entity behavior analytics (UEBA) can be leveraged to safeguard organizations. In this fourth post of the series, we'll examine cyberattacks that threaten the education sector.
At first glance, organizations in the education sector don't seem like a typical target for a cyberattack. After all, an educational institution may not have as deep a pocket as organizations from other industries, and most of its users are young students. However, upon closer examination, educational organizations are lucrative one-stop shops for cybercriminals looking to swipe sensitive data.
Educational institutions contain a hoard of personal information such as names, addresses, Social Security numbers, financial details, and even critical medical conditions of the students enrolled. And in today's world where numerous higher educational institutions collaborate with both the government and private sector to undertake research, state-sponsored cyberattacks with geopolitical motives are a constant threat.
IT security administrators working with educational institutions navigate a challenging threat landscape comprising of diverse devices and assets that need around the clock protection. Let's discuss some of the threats that can bring down an educational institution, and how UEBA can help combat them.
Locked out
It felt like the 90's at Greendale Community College with assessments being conducted on pen and paper, professors marking students' attendance manually, and librarians racing up and down the aisles to help students locate books. A massive ransomware attack had crippled Greendale's network, plunging the college into the pre-internet era.
 Ransomware attack causes network shutdown at Greendale Community College.
Ransomware attack causes network shutdown at Greendale Community College.
Greendale fell prey to a malvertising campaign that introduced locker ransomware into the organization's network. Malvertising is a technique hackers use to plant malware within online advertisements to infect computers. A user within the college clicked on one of these malicious advertisements, which redirected them to a different URL from where the ransomware payload was downloaded without the user's knowledge, giving hackers access to the network. Once hackers gained access, they scanned the network for shared resources that had weak passwords or unsecured hardware and from there, moved laterally in the network until finally bringing the organization to a standstill.
While Greendale decided not to pay the ransom and is fervently working towards bring its systems back online, the mishap could have been completely prevented if the college had utilized a UEBA solution to protect its network. UEBA could have spotted the pattern and count anomalies right when the malware began executing changes on numerous files in the first victim's computer, and alerted the IT administrators to take corrective action. The device could have been easily quarantined from the college's network, halting the outbreak and limiting the damage.
Phishing for PII
Ryan Demming is an admissions officer at the Brookefield Academy, one of the most established private boarding schools in the United States. Its peak admissions season in late July when Ryan receives an email with the subject, "Offer acceptance - Reg," containing some questions about how to accept the offer of admission on the school's portal. Ryan doesn't realize that this is a spear phishing attack.
 Attackers employ spear phishing to gain access to the school's critical database.
Attackers employ spear phishing to gain access to the school's critical database.
Once he opened the email, the embedded malware, capable of wiring data to the attackers via email, was downloaded into Ryan's system. The malware began executing numerous commands in PowerShell to access the database containing student information. This sensitive database containing students' personally identifiable information, copies of educational certificates, medical history, and more, can be used to perform identity theft and extortion, or even to commit organized crime.
Luckily, Brookefield's UEBA solution was able to avert the malware data exfiltration attempt before it could email the copied database to the cyberattackers' command and control (C&C) server. The UEBA solution increased the risk score of Ryan's computer drastically when it spotted multiple PowerShell commandlets that were executed in quick succession to access and copy student databases, alerting the school's cybersecurity personnel and helping them prevent the attack.
The devil in disguise
Most educational institutions restrict internet use to prevent access to unauthorized sites and applications. The University of Hudson, one of the country's premier institutions, is known for its high research output, breaking ground recently for innovation in regenerative medicine. Several pharmaceutical companies were trying to get their hands on the research methodology and outputs that the university held, making it a prime target of intellectual property theft.
Samantha Fernando, an undergraduate in the school of life sciences, is unaware of the cybercriminals looking to gain access to the department's network, and downloads a virtual private network (VPN) from an unverified source to access blocked web pages. The VPN, originally a Trojan malware, was programmed to move laterally in the network, gain access to the server that housed research files, and transmit the files to the criminals' C&C server. Inadvertently, Samantha became the point of entry exposing the entire network.
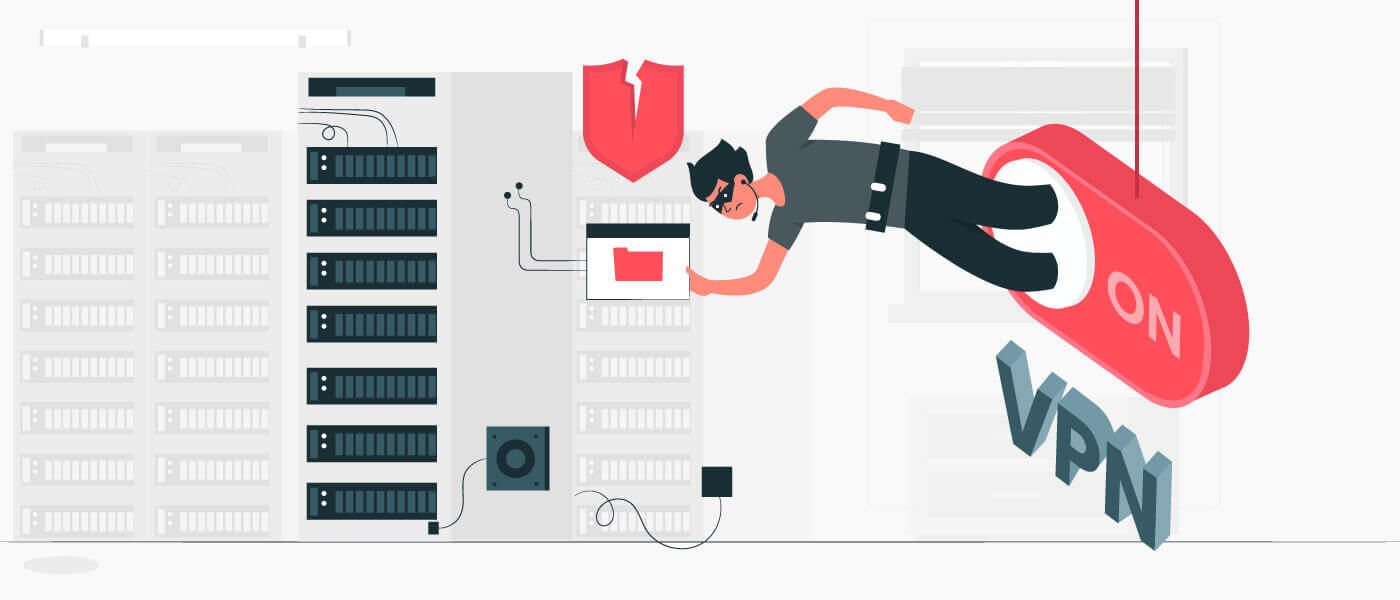 A Trojan malware disguised as VPN is used by cybercriminals penetrate the university's network.
A Trojan malware disguised as VPN is used by cybercriminals penetrate the university's network.
However, the criminals didn't succeed in their pursuit to steal research files. The UEBA solution that the university employed spotted the sudden and unusual count of port scan events happening in the network and increased the risk score of the entities from which the event was happening. The sudden increase in the risk score of numerous entities connected to the network alerted the network administrators to suspicious activity, who investigated the incidents and terminated the malware, effectively mitigating the malware intrusion before it could reach critical servers.
Many schools and colleges do well in imparting cybersecurity education to their students, but fall short in practically implementing those principles on their institutions' network. With the number and intensity of cyberattacks starkly increasing in this field, educational institutions that don't have adequate cybersecurity measures in place should be worried.
By leveraging intelligent security solutions such as UEBA, universities and schools can guard their networks from various cyberattacks that can jeopardize the institution and its stakeholders alike.