Download a complimentary copy of the report here.
Many recent cyberattacks substantiate that granting internal IT staff and third-party contractors uncontrolled access to critical systems can cause serious security problems and increase risk.
The more users with access to privileged credentials, the higher the risk that attackers could get unrestricted access to the IT network. Organizations that provide unfettered access to all users often lack visibility into the operations performed with such access. Limiting and controlling privileged access must be an essential part of IT security workflows to minimize the risk of uncontrolled privileged access.
An access control workflow helps administrators provide authorized, controlled access to remote resources. In-depth audit trails that capture all the details of remote access, including who requested what access, why, and who approved the request, also help in fortifying the access control workflow.
Access Manager Plus allows users to restrict access to the connections they’ve added. Unless the request to access a particular connection is approved by the owner of the connection, others will not be able to launch a remote session to that connection or view its password.
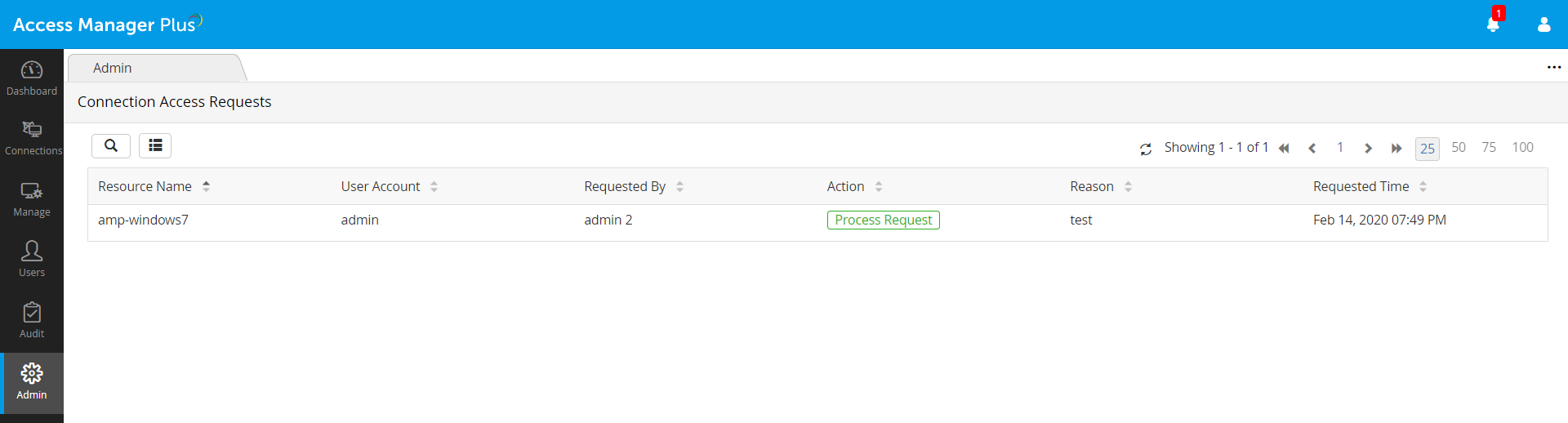
You can mandate users requiring access to a remote connection to raise a request and provide a credible reason. This allows the connection owner to scrutinize access requests before approval and reject inappropriate requests.
Upon authorizing access requests, provision users with temporary access to the remote connection for a specified time frame. By default, Access Manager Plus automatically revokes a user’s access after 30 minutes from the time they check out a password. Through session shadowing, administrators can detect a suspicious session in real time and forcefully check in the corresponding password before the stipulated time expires.
Access Manager Plus enables administrators to prevent multiple users from simultaneously accessing a particular connection. Only one user can check out the password for a remote connection at a time. If another user requests access to a password that’s in use and their request is approved, they’ll be allowed access only after the current user checks in the password.
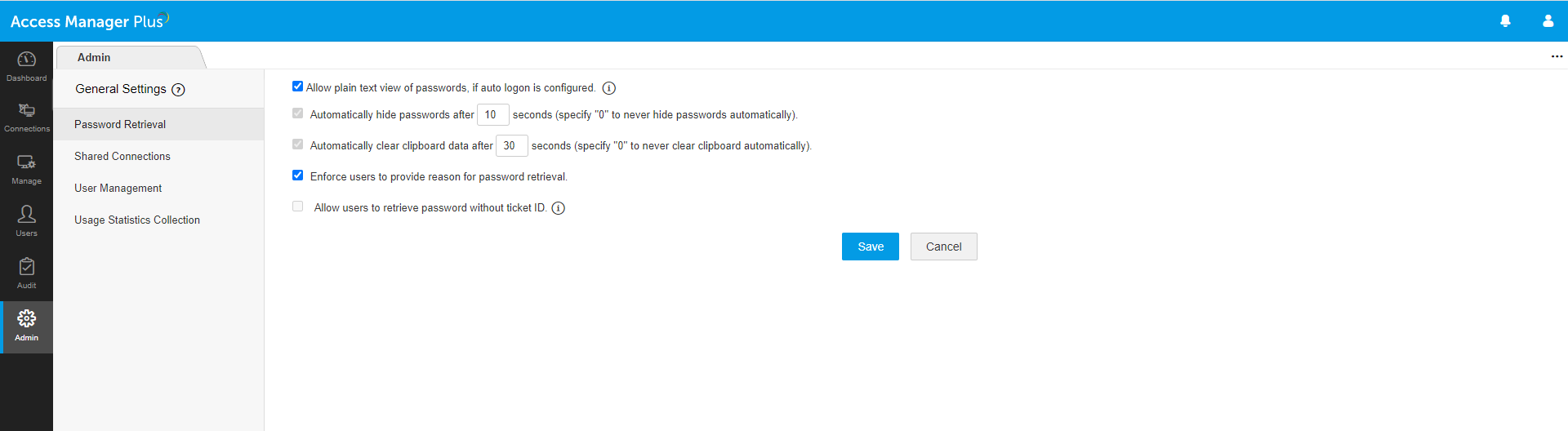
For further security, administrators can prevent the exposure of passwords in plaintext while providing access to the desired connections. In such cases, users will be able to launch a remote connection through Access Manager Plus’ auto-logon feature. If plaintext view of passwords is enabled, administrators can choose to hide the passwords after a specified time.